Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Multi-tenancy Support
In CSA, an organization is an entity such as a Company, Business Unit, Department, or Group that is defined by the CSA Administrator. The Administrator also determines a member's entry point into the cloud and associates each member with services and resources. The membership in an organization is determined by the Organization's Identity Management configuration. CSA accesses the Identity configuration to authenticate the user's login credentials with OpenLDAP or Microsoft Active Directory.
CSA identity management (IdM), apart from the primary authentication with OpenLDAP or Microsoft Active Directory also supports the configuration of secondary authentication with OpenStack Identity (keystone) service to enable an integration account or transport user to perform OpenStack actions on behalf of another user. On successful secondary authentication against keystone, a Keystone Trust ID is generated using the authenticated user as the Trustor and the configured integration account as the Trustee.
In OpenStack, a project is a logical grouping of users, and is used to define quotas and access to virtual machine images.
In OpenStack, an administrator implements multi-tenancy by manually mapping CSA organizations to OpenStack projects. This mapping is established through the use of a directory service: OpenLDAP or Microsoft Active Directory.
Note Mapping can be established manually without configuring Keystone to use OpenLDAP or Microsoft Active Directory.
The following table lists the example for supported mapping:
| CSA | OpenStack |
|---|---|
|
CSA Organization (Marketing)
|
Project (MARKETING)
|
|
CSA Organization (Engineering)
|
Project (ENGINEERING)
|
Mapping organizations to project and identity management through secondary authentication using keystone ensures that all subscription requests from an Organization's user are accomplished for the users and the corresponding project.
CSA organization user can then use the Marketplace Portal to check out an offering and create a subscription in CSA market place portal. CSA logs in to OpenStack using the relevant project user credentials and orchestrates the provisioning of instances.
OpenStack-Multi-Tenant Support v4.0
This design supports multi-tenancy in the form of subscriber option: Enable User Impersonation Mode and Tenant Name.
If the User Impersonation Mode is set to false, the tenant is fetched from Provider (Tenant/ Project is entered in Provider). If the User Impersonation is set to true, the list of OpenStack tenants that the user has access to is displayed. The provider service access point must be configured with Keystone API v3 endpoint.
CSA administrator must update this option with appropriate value while creating service offering and make it invisible to consumers.
Note If the service design is manually imported, make sure that all the JSPs in the service design and os-common-pp-v3.jsp are placed in the following location:
<CSA Installation path>\<CSA jboss path>\standalone\deployments\csa.war\propertysources
Implement Multi-tenancy
Follow the steps to implement multi-tenancy:
-
Enable Keystone authentication in IdM:
Set
idm.keystone.enabled = truein the fileC:\Program Files\Hewlett-Packard\CSA\jboss-as\standalone\deployments\idm-service.war\WEB-INF\spring\applicationContext.properties. -
Create an OpenStack Resource Provider in CSA Management console:
Provide the Service Access Point for Keystone service and the IdM Keystone Integration account credentials.
Specify the following properties for the OpenStack provider:
- Enter the project in OpenStack while provisioning sequence designs in which
enableUserContextis set to False for every OpenStack component in the design. If for all OpenStack designs,enableUserContextis set to True, then the project is left empty and the subscriber must select the project at provisioning time from the set of projects to which the subscriber is authorized. - Domain - Enter the domain in OpenStack. This domain must be configured for authentication in the same manner as the consumer organizations for which this provider is used.
- Transport Token - If checked a domain-scoped transport token is used for communication with OpenStack. If unchecked, a project-scoped transport token is used. The provider user must have administrative rights on the domain in order to use domain-scoped transport tokens.
- Enter the project in OpenStack while provisioning sequence designs in which
- Setup organization in CSA with a directory service endpoint: OpenLDAP or Microsoft Active Directory that is also configured in the OpenStack Keystone instance.
Map LDAP of the CSA organization to LDAP of OpenStack Keystone instance and identity management secondary authentication with Keystone. Ensure that all subscription requests from organization users are fulfilled in the context of user and the selected project.
The sequence of operations performed in multi-tenancy is shown in the following figure:
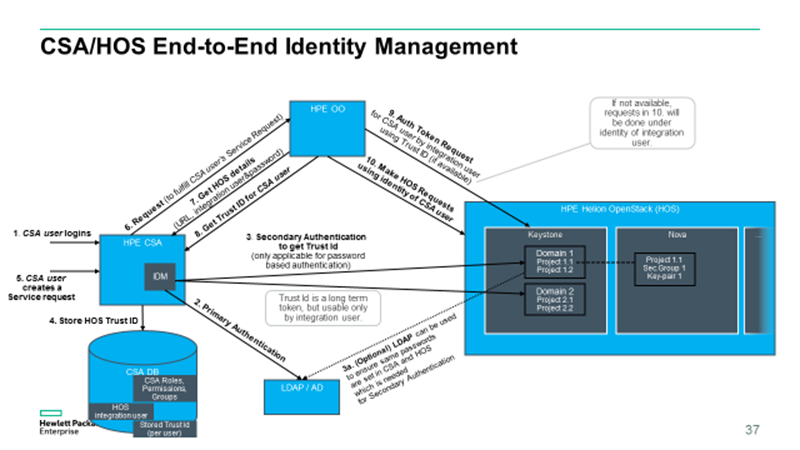
In general, this feature works as follows:
- After a successful authentication against one of the primary mechanisms (LDAP, Active Directory), IdM attempts to authenticate against a secondary mechanism (Keystone) using the same credentials.
- After successful authentication against Keystone, it generates Keystone trust IDs using the authenticated user as the Trustor and the configured integration account (provider user) as the Trustee, for all the OpenStack project that the user has access to.
- Choose one of the project and associated Keystone trust ID and use it to generate a Keystone impersonation token so that configured provider account can perform OpenStack actions on behalf of the Trustor.
Note Integration account configured in IdM for secondary authentication and OpenStack provider configured in CSA should be the same.
Verify Secondary Authentication
Follow the steps after IdM secondary authentication:
-
Either setup the organization’s LDAP server as the LDAP back-end for CSA or replicate all the organization’s users in Keystone (same username / password).
All Keystone users must belong to a project whose name exactly matches the CSA organization name used to log in. These names are case-sensitive, that is, a Keystone project name 'project_name' will not match a CSA organization ID 'PROJECT_NAME'.
To find the actual name:
- Log on to CSA admin console and click Organizations.
-
Go to the respective organization, and click General Information. The Organization URL is displayed.
The last word in the URL after /org/ is the organization name which must exactly match the project name in OpenStack.
-
Log on to CSA Organization consumer portal (example: ENGINEERING/engg_user1) and verify the IdM logs at
<CSA install path>\<Jboss…>\standalone\log\hpcloud-idm-service.log
For example:
2014-11-13 16:02:29,731 [http-/0.0.0.0:8444-7] INFO com.hp.ccue.identity.authn.MultiTenantAuthenticationProvider - Authentication succeeded for user engg_user1
2014-11-13 16:02:30,786 [AsyncAppender-Dispatcher-Thread-80] INFO com.hp.ccue.identity.audit.CSAAuditor - Audited event: {1415923350685:AUTHENTICATION:LOGIN:IDM:engg_user1:ENGINEERING:CSA42-OO1020:null:Authentication success}
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to csl_doc_feedback@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





