Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
- Universal CMDB Login Authentication
- Setting Up an Authentication Method
- Enabling Login to Universal CMDB with LW-SSO
- Enabling Login to Universal CMDB with SAML
- Setting a Secure Connection with the SSL (Secure Sockets Layer) Protocol
- Using the JMX Console to Test LDAP Connections
- How to Enable HTTP Communication for Universal CMDB
- Hybrid User Management with Multiple User Repositories
- How to Define LDAP Servers and Enable LDAP Authentication Method
- LDAP Authentication Settings - Example
- Example: How to Configure LDAP for Sun ONE Directory Server in UCMDB Server
- Example: How to Configure Dynamic LDAP Groups
- Retrieving Current LW-SSO Configuration in Distributed Environment
- User Lockout Mechanism
Example: How to Configure LDAP for Sun ONE Directory Server in UCMDB Server
This example focuses on Sun ONE Directory Server.
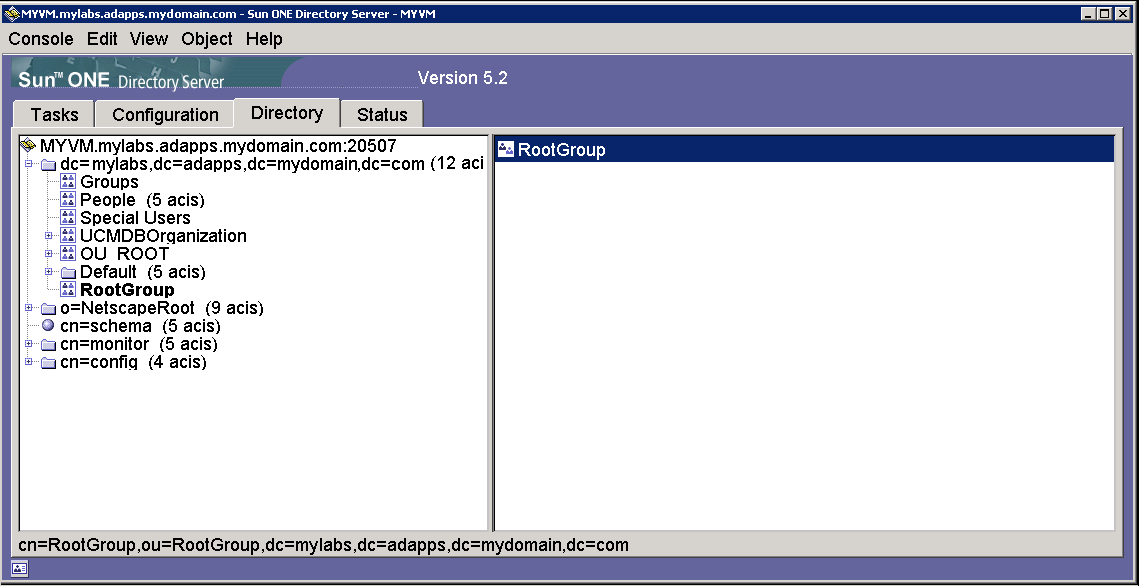
Not everything from the server will be used. Focus on the following:
HM: The host machine: myvm.mylabs.adapps.mydomain.com
PORT: The port of the Active Directory server: 20507
DC: The domain component (path to the organization units): dc=mylabs,dc=adapps,dc=mydomain,dc=com
OU: In this example, the following organizational units will be used:
- Groups: The non-root groups
- People: The users
- RootGroup: The root groups
Your Active Directory server does not have to be exactly like this one. This is just an example to help you understand what the configurations required by UCMDB mean.
In what follows if we use upper case it means we refer to the above fields.
In UCMDB there are a big list of parameters that need to be set for connection to an LDAP server.
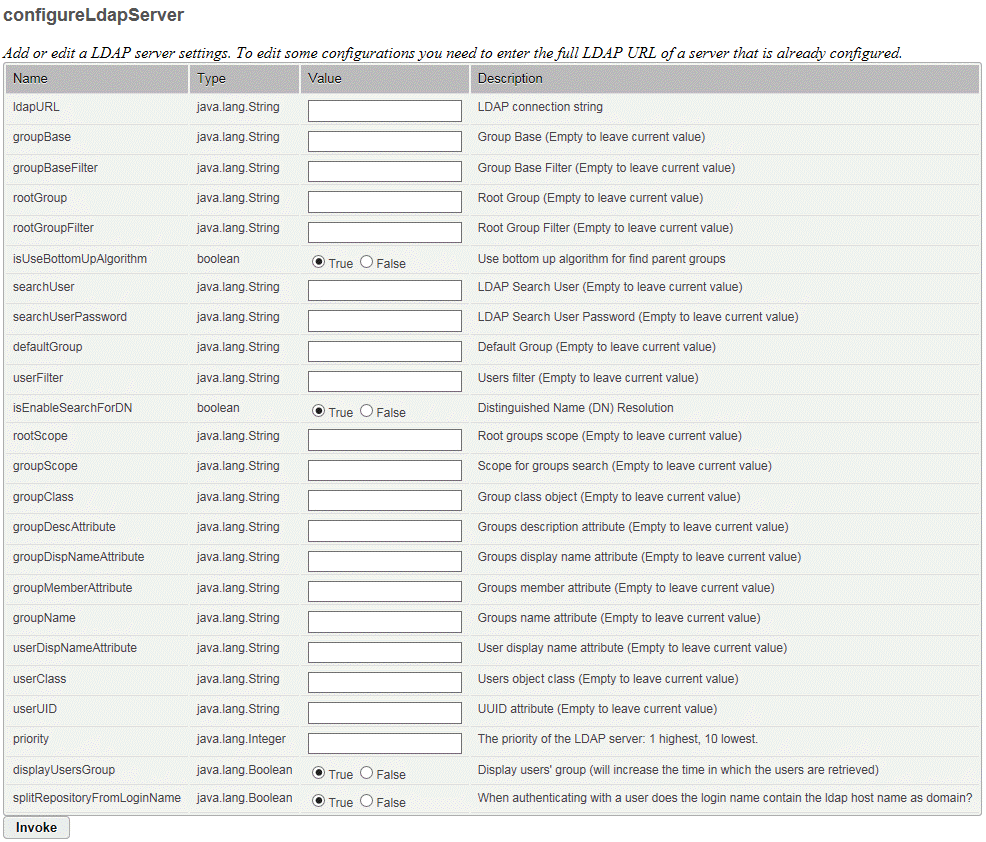
Here let's take each of them and see what they mean and how to configure them.
| LDAP server setting name | What the setting means and how to configure it |
|---|---|
| ldapURL |
This parameter consists of four parts:
The value for this parameter should follow the following format: <Protocol>://<HM:PORT>/<ou=People,DC> In this example, it results in: ldap://myvm.mylabs.adapps.mydomain.com:20507/ou=People,dc=mylabs,dc=adapps,dc=mydomain,dc=com Note Having multiple user repositories (LDAP servers) on the same machine is not supported. We use the host name as the unique identifier for those resources. This means that we cannot have multiple LdapServers with the same host name (myvm.mylabs.adapps.mydomain.com in this example). |
| groupBase |
This represents the path to the groups. In this example there are two different OUs, one for the root groups (ou=RootGroup,DC) and one for other groups (ou=Groups,DC), therefore the groupBase parameter needs to be set to the parent of both: DC. So it results in something like the following: dc=mylabs,dc=adapps,dc=mydomain,dc=com |
| groupBaseFilter |
Set the filter for the groups. In SunONE a static group inherits from the groupOfUniqueNames object class, so the value for the groupBaseFilter parameter should be the following: (objectclass=groupOfUniqueNames) |
| rootGroup |
This represents the path to the root groups: ou=RootGroup,dc=mylabs,dc=adapps,dc=mydomain,dc=com |
| rootGroupFilter |
Set the filter for the root groups. We use the groups filter again: (objectclass=groupOfUniqueNames) If we would have all the groups (root groups + other groups) in the same OU, then we could use this filter to define which groups are the root ones, for example groups whose name start with “Group”: (&(objectclass=groupOfUniqueNames)(cn=Group*)) |
| isUseBottomUpAlgorithm |
The algorithm used to traverse the groups. In this example, it is set to: False |
| searchUser |
This represents the admin user that will be used to connect to the LDAP server. In this case: cn=Directory Manager |
| searchUserPassword |
Specify the password for the admin user: mypw |
| defaultGroup |
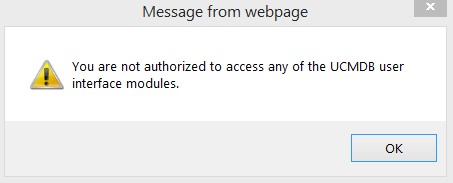
If we login with an LDAP user on UCMDB, what permissions will it have? Here we specify the UCMDB group that will be used if no other permissions are set for an LDAP user. So we need a valid UCMDB group name: UCMDBGroup If this group does not exist or it does not have enough permissions, when trying to log in on UI, you will see an error message:
Note The UCMDB group can be created after the LDAP Server is configured. |
|
userFilter |
Like we had a filter for groups, we also have one for users. This defines which entities from the LDAP server we consider to be users. In our case the users inherit from the inetOrgPerson object class: (objectclass=inetOrgPerson) |
| isEnableSearchForDN |
If true when searching for information on the LDAP server, it resolves a distinguished name to a domain controller that holds the entry for that name. Here we set it to: True |
| serchRetriesCount |
Let’s say we want to search for a user but the LDAP server is down for 1 millisecond. This field specifies how many times we will retry the search if the connection is down. We set it to: 5 |
| rootScope |
The scope of the search for the root groups. We use: sub |
| groupScope |
The scope of the search for the non-root groups. We use again: sub |
| groupClass |
Here we set the class from which the groups inherit. As we have already seen in our case this is: groupOfUniqueNames |
| groupDescAttribute |
The attribute that defines the description of the groups. For us it is: desc |
| groupDispNameAttribute |
The attribute that defines the display name of the groups. For us it is: cn |
| groupMemberAttribute |
The group members are found using this attribute. In our case: uniqueMember |
| groupName |
The attribute that defines the group name. For us it is: cn |
| userDispNameAttribute |
The attribute that defines the user display name. For us it is: cn |
| userClass |
The class from which the users inherit. We use: inetOrgPerson |
| userUID |
The attribute that defines the user unique ID. We have: uid |
| priority |
Each user repository has a priority defined. This field is used every time a host name is not specified in an operation. For example if we log in with a user without specifying the server that contains the user, we will go on all user repositories in priority order. If multiple LDAP Servers are configured with the same priority, they will be checked in the order they were configured. If a user with that name is found on a server we will not go further. For UCMDB internal store the out-of-the-box priority is 1. Here we will use: 5 |
| displayUsersGroup |
This is related to the new feature of querying the users using chunks. If this field is on true and we search for users when we get the results we will also receive the name of the group that contains that user. This will obviously impact performance because we request more data from the LDAP server. We will set it on: False |
| splitRepositoryFromLoginName |
When authenticating with a user, whether the user login name should contain the LDAP host name as domain or not. Here we set it on: True |
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to cms-doc@microfocus.com.
Help Topic ID:
Product:
Topic Title:
Feedback: