Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
FIPS 140-2 Compliance Statement
HPE IT Business Analytics (ITBA) complies with the Federal Information Processing Standard 140-2 (FIPS 140-2), which defines the technical requirements to be used by Federal Agencies when these organizations specify cryptographic-based security systems for protection of sensitive or valuable data. The compliance of ITBA with FIPS 140-2 is ensured by:
- Integrating validated and NIST-certified third party cryptographic module(s), and using the module(s) as the only provider(s) of cryptographic services;
- Using FIPS-approved cryptographic functions;
- Using FIPS-approved and NIST-validated technologies;
- Using security controls defined in NIST 800-53, prescribed for cryptographic modules by FIPS 140-2 and applicable for ITBA design, implementation and operation.
About IT Business Analytics
-
ITBA is a young product and considered to be the leading IT product today, measuring and optimizing the cost, risk quality and value of IT services and processes. The first release was on June 2011. ITBA biggest differentiator from the competition is usability and content. ITBA has tight integrations with HPESW products. ITBA 10 is already bundled with Project and Portfolio Management (PPM), Service Manager (SM), Application Lifecycle Management (ALM), Cloud Service Automation (CSA), and Amazon Web Services (AWS). ITBA is currently in the middle of transition from being a Dashboard tool for senior managers to a leading Business Analytics tool for mid-layer managers as well. ITBA is on top of Vertica DB, meaning that it will deal with large amount of data. It has amazing Time-to-Value and provides a stable foundation for Self-Service Analytics capabilities.
ITBA is in competition with very powerful self-service analytic tools such as Tableau, QlikView, which provide easy ways to manage, view and analyze the data, along with BI tools such as VMWare ITBM and MooD BI.
- For more details about how ITBA implements FIPS 140-2 requirements, see ITBA and FIPS140-2.
About FIPS 140-2
The Federal Information Processing Standards Publication (FIPS) 140-2, “Security Requirements for Cryptographic Modules,” was issued by the National Institute of Standards and Technology (NIST) in May, 2001. The standard specifies the security requirements for cryptographic modules utilized within a security system that protects sensitive or valuable data. The requirements can be found in the following documents:
-
SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES:
http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf
-
Annex A: Approved Security Functions for FIPS PUB 140-2, Security Requirements for Cryptographic Modules
http://csrc.nist.gov/publications/fips/fips140-2/fips1402annexa.pdf
FIPS 140-2 Compliant Module and Technologies
The benefits of using FIPS 140-2 validated crypto module is that the crypto algorithms are deemed appropriate and that they perform the encrypt/decrypt/hash functions correctly.
Modes of Operation
ITBA can be configured and can operate in two modes:
- FIPS-compliant mode. Supports FIPS 140-2 compliant cryptographic functions. The default FIPS 140-2 compliant algorithms and key length are configurable. It provides flexibility for products integration and meeting the higher cryptographic security standards of NSA Suite B cryptography (http://www.nsa.gov/ia/programs/suiteb_cryptography/) in addition to FIPS 140-2 compliance.
- Standard mode. Non-FIPS 140-2 compliant mode which utilizes existing cryptography available without 3rd party FIPS 140-2 crypto modules.
FIPS 140-2 Validated Third Party Module
ITBA is integrated with 3rd party FIPS 140-2 validated cryptographic module RSA BSAFE Crypto-J. Its compliance was validated according to Cryptographic Module Validation Program (CMVP http://csrc.nist.gov/groups/STM/cmvp/index.html) and certified on Intel/Windows with Sun JRE 6.0 platform by NIST (http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/140val-all.htm#1786 ). When ITBA is configured to operate in FIPS-compliant mode, its functions and procedures - like SSL/TLS connections, which require cryptography such as secure hash, encryption, digital signature etc. – make use of the crypto services provided by RSA BSAFE Crypto-J. It supports FIPS 140-2 compliance of ITBA.
Details about how to configure ITBA and its components to conform to FIPS 140-2 standard appear in the installation guides for the product(s):
- ITBA ..
TLS/SSL3.x
All the ITBA components communications are secured with FIPS-compliant Transport Layer Security TLS1.0/SSL3.1 or higher. They are relying on FIPS 140-2 approved hash algorithms and symmetric and asymmetric ciphers.
- TLS handshake, key negotiation and authentication provides data integrity and is making use of secure hash, asymmetric key cryptography and digital signature.
- TLS encryption of data in transit provides confidentiality and making use of symmetric cryptography.
Secure Hash
Per FIPS 140-2 standards, ITBA, in the FIPS 140-2 compliant mode, can be configured to use the following secure hash algorithms:
SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 and SHA-512/256
Symmetric Cryptography
Per FIPS 140-2 standards, ITBA, in the FIPS 140-2 compliant mode, can be configured to use the following symmetric key algorithms:
AES (ECB, CBC, CFB, OFB, CTR, CCM, GCM, XTS) [128, 192, 256 bit key sizes]
Triple-DES (ECB, CBC, CFB, OFB)
Message Digest
Per FIPS 140-2 standards, ITBA, in the FIPS 140-2 compliant mode, can be configured to use the following digital signature algorithms:
SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256
Digital Signature
Per FIPS 140-2 standards, ITBA, in the FIPS 140-2 compliant mode, can be configured to use the following digital signature algorithms:
RSA X9.31, PKCS #1 V.1.5, RSASSA-PSS; DSA; ECDSA
ITBA and FIPS140-2
ITBA is expected to operate on General Purpose Systems with no additional physical security controls. RSA BSAFE Crypto-J crypto module installed on such platforms provides validation to Level 1 FIPS 140-2 compliant crypto services.
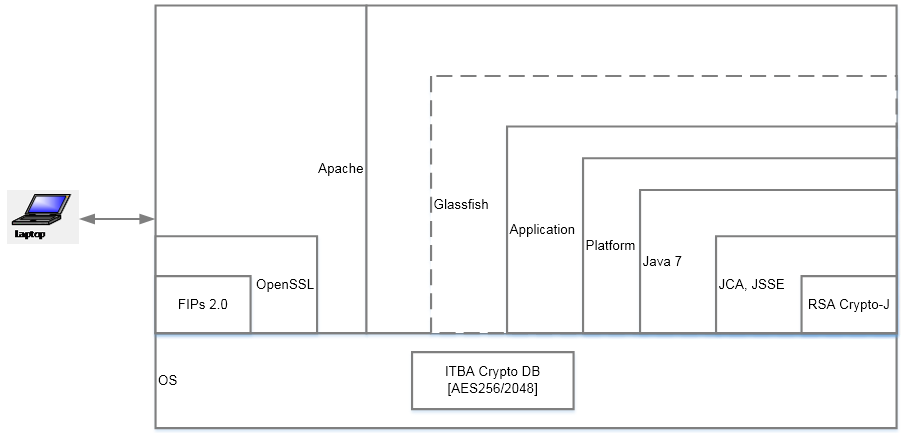
FIPS 140-2 Architecture
Supported Platforms
Refer to the ITBA . document for a comprehensive list of supported platforms.
Also refer to the document ITBA . for a comprehensive list of 3rd Party SW used by ITBA including the JDK.
Supported Modes and Cryptography
- FIPS mode. Supports FIPS 140-2. In this mode, all cryptographic functions, default algorithms and key length are configurable.
- Standard mode. Non-FIPS 140-2 compliant mode, with standard existing cryptography available without 3rd party FIPS 140-2 crypto modules.
Key Management
Many aspects of key management, such as random number and key generation, are provided by functions of RSA BSAFE Crypto-J crypto module, thus meet FIPS 140-2 compliance requirements. The application-specific key management functions include
- Key Generation. All private and public key used by ITBA are generated during installation time. This is an automatic process which does not require any inputs from the user.
- Key Storage. The private keys are stored in a 3DES encrypted, password protected file.
- Key Protection. The password to the ITBA management DB is required to access its contents.
- Key Access. Only a valid user in ITBA server can access ITBA management.
Design Assurance
The RSA Bsafe Crypto-J module is packaged in ITBA and installed by the ITBA installer as JAR files provided by the vendor. The configuration parameters to use the crypto modules in ITBA and parameters to enable or disable FIPS mode is supplied to the modules as part of the Java runtime environment security configuration. The crypto modules are loaded by the ITBA modules that use them for FIPS enabled crypto functions by loading the modules as their primary crypto providers. This vendor recommended method of priority loading is also controlled by the Java Runtime security settings. Further, the RSA Bsafe Crypto-J modules are loaded only if FIPS mode is enabled.
FIPS mode is enabled in ITBA during installation. It is one of the installation interview questions. Once enabled, FIPS mode cannot be disabled.
Risk Mitigation
Physical or remote access to ITBA server and access to root user password is required to gain access to the password protected file and the crypto modules. Further, the password to the management DB is required to access its contents.
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to SW-Doc@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback: