Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Regulatory policies
The out-of-the-box (OOTB) regulatory policies provide predefined values for audit and remediation according to guidelines such as CIS, PCI, or SOX.
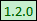
The policies shown in the following table are currently available as free non-subscription content for HPE ITOC 1.20.
| Name | Description | Prerequisite Control Library | Applicable ITOC Release |
| CIS CentOS Linux 7 Benchmark v1.1.0 | CIS CentOS Linux 7 Benchmark provides prescriptive guidance for establishing a secure configuration posture for CentOS version 7.0 running on x86 and x64 platforms. | Control Library for UNIX | 1.00 and later |
| CIS Red Hat Enterprise Linux 5 Benchmark v2.1.0 | CIS Red Hat Enterprise Linux 5 Benchmark provides prescriptive guidance for establishing a secure configuration posture for RHEL versions 5.x running on x86 and x64 platforms. | Control Library for UNIX | All |
| CIS Red Hat Enterprise Linux 6 Benchmark v1.3.0 | CIS Red Hat Enterprise Linux 6 Benchmark provides prescriptive guidance for establishing a secure configuration posture for RHEL versions 6.x running on x86 and x64 platforms. | Control Library for UNIX | All |
| CIS Red Hat Enterprise Linux 7 Benchmark v1.0.0 | CIS Red Hat Enterprise Linux 7 Benchmark provides prescriptive guidance for establishing a secure configuration posture for RHEL versions 7.x running on x86 and x64 platforms. | Control Library for UNIX | 1.00 and later |
| CIS SUSE Linux Enterprise Server 11 Benchmark v 1.0.0 | CIS SUSE Linux Enterprise Server 11 Benchmark provides prescriptive guidance for establishing a secure configuration posture for SUSE Linux Enterprise Server (SLES) version 11 running on x86 and x64 platforms. | Control Library for UNIX | All |
| CIS Ubuntu 12.04 LTS Server Benchmark v1.0.0 | This document provides prescriptive guidance for establishing a secure configuration posture for Ubuntu 12.04 LTS Server. | Control Library for UNIX | All |
| CIS Microsoft Windows Server 2012 v1.0.0 | CIS Microsoft Windows Server 2012 Benchmark v1.0.0 provides prescriptive guidance for establishing a secure configuration posture for CIS Microsoft Windows Server 2012. | Control Library for Windows | All |
| CIS Microsoft Windows Server 2012 R2 v1.1.0 | CIS Microsoft Windows Server 2012 R2 Benchmark v1.1.0 provides prescriptive guidance for establishing a secure configuration posture for CIS Microsoft Windows Server 2012 R2. | Control Library for Windows | 1.00 and later |
| CIS Apache HTTP Server 2.4 v1.2.0 | This document is intended for system and application administrators, security specialists, auditors, help desk, and platform deployment personnel who plan to develop, deploy, assess, or secure solutions that incorporate Apache HTTP Server 2.4 running on Linux. | Control Library for Software | 1.10 |
| CIS Oracle MySQL Community Server 5.6 v1.0.0 | This document, CIS Oracle MySQL Community Server 5.6 Benchmark, provides prescriptive guidance for establishing a secure configuration posture for MySQL Community Server 5.6. | Control Library for Software | 1.10 |
| CIS Apache Tomcat Server 6.0 Benchmark v1.0.0 | This document is intended for system and application administrators, security specialists, auditors, help desk, and platform deployment personnel who plan to develop, deploy, assess, or secure solutions that incorporate Apache Tomcat on a Linux platform. | Control Library for Software | 1.10 |
| JBoss Application Server 7 Hardening Guidelines | This policy is intended for organizations or individuals that are using JBoss Application Server 7 (in standalone or domain mode) on secure production systems. | Control Library for Software | 1.10 |
| CIS Security Configuration Benchmark for Oracle Database Server 11g, version 1.0.1 | CIS Security Configuration Benchmark for Oracle Database Server 11g provides prescriptive guidance to secure Oracle database from conventional OOTB threats. | Control Library for Oracle 10g/11g | All |
| CIS Benchmark for Oracle 9i/10g, Version 2.01 | CIS Security Configuration Benchmark for Oracle Database Server 9i/10g provides prescriptive guidance to secure Oracle database from conventional OOTB threats. | Control Library for Oracle 10g/11g | All |
| Payment Card Industry (PCI) Data Security Standard version 3.0.0 | The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. This policy is applicable only for the following resource types - Platform Resources: Microsoft Windows Server 2008 R2, 2012, Red Hat compatibles and SuSE compatibles, Ubuntu 12.04. Software Resources: Apache HTTP 2.4, Apache Tomcat 6.x, MYSQL Community Server 5.6, JBoss AS 7.x. | Control Library for Windows and Control Library for UNIX | 1.00 and later |
| NIST SP 800-53 Revision 4 (FISMA) | Audit Policy for NIST Special Publication 800-53 Revision 4 - Recommended Security Controls for Federal Information Systems and Organizations. This policy is applicable only for the following resource types - Microsoft Windows Server 2008 R2, 2012, 2012 R2 , Red Hat compatibles and SuSE compatibles, Ubuntu 12.04. | Control Library for Windows and Control Library for UNIX | 1.00 and later |
| NIST SP 800-66 Revision 1 (HIPAA) | Audit Policy for NIST Special Publication 800-66 Revision 1 - Recommended Security Controls for Health Insurance Portability and Accountability Act. This policy is applicable only for the following resource types - Red Hat compatibles and SuSE compatibles. | Control Library for Windows and Control Library for UNIX | 1.00 and later |
| CIS MS SQL 11 Benchmark v1.2.0 | This policy, CIS MSSQL Benchmark v1.2.0, provides prescriptive guidance for establishing a secure configuration posture for CIS MS SQL version 11. | Control Library for MS SQL Server | 1.00 and later |
| CIS DB2 Database Server 10.5 Benchmark v1.1.0 | This policy, CIS DB2 10.5 Benchmark v1.1.0, provides prescriptive GUIDance for establishing a secure configuration posture for DB2 Database Server 10.5. | Control Library for DB2 Database Server | 1.00 and later |
The following table shows which platforms and software resources are covered in the PCI, FISMA, or HIPAA policies in the ITOC 1.20 release:
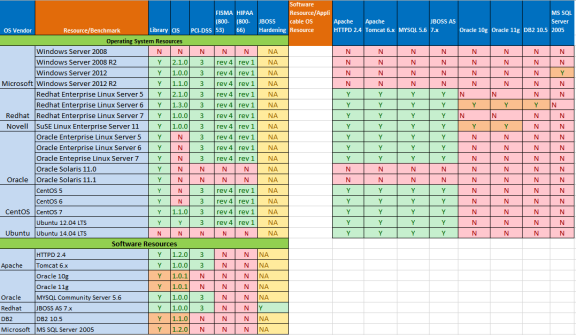
Table Legend:





For all benchmark policies, the corresponding compliance control library is a prerequisite. Please import the respective control library before importing any benchmark policy.
All rules in a policy are set with audit, remediation parameter values as recommended by the benchmark document. There are some rules for which the benchmark suggests to set the value that is consistent with the security and operational requirements of an organization.
Such requirements in OOTB policies and the values provided in the audit and remediation parameters are intended as an example only or as a default value set as per the benchmark recommendation. Please edit rules to include the specific values that are consistent with the security and operational requirements of your organization.
Please refer to the regulatory policy documentation for requirements that need specific values to be configured.
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_itoc_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





