Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Minimum Windows and VMware permissions for ESXi audit functions
ESXi audits use an integration user for listing ESXi targets and servers, and running the PowerCLI scripts. You might have already created this user if you use SA VMware virtualization. This section describes how to control access for the integration user.
- Minimum Windows and VMware permissions for ESXi audit functions
- Minimum Windows and VMware permissions for ESXi audit functions
Windows permissions
This section describes the user Windows account required to use ESXi servers.
- Create a non-administrator user account, for example, SAUser.
- Minimize this user’s access in accordance with your company’s security policies.
For more information about virtualization users, see "Virtualization management" in the SA 10.51
VMware permissions
This section describes VMware roles required to use ESXi servers. These steps include: setup a VMware role with host-only access, create a permission with our integrated user, in that role, and apply it to all the hosts that you want to manage.
- Create a VMware role with all privileges and host-only access.
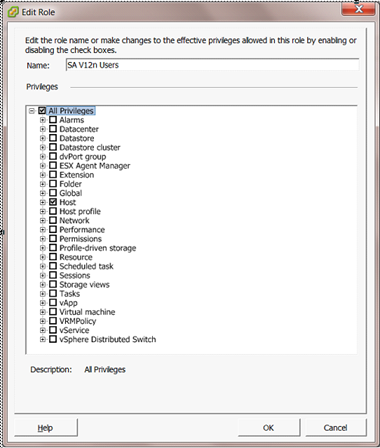
- Select the Hosts tab.
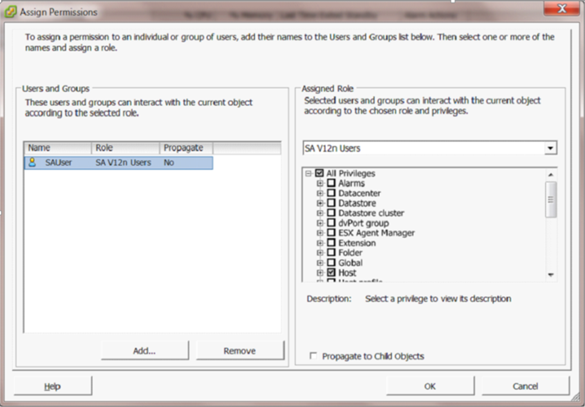
- Assign permissions:
- Right-click on the selected hosts to bring up the context menu.
- Click Add Permission…
- Select the role created in step 1.
- Add the integrated user.
- Uncheck the Propagate to Child Objects box (if permissions are propagated to the VMs, even host-only permissions, then those VMs will appear in SA as agentless devices).
- Add the vCenter to SA Virtualization. If the vCenter has already been added, run the Reload Data job.
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_sa_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





