Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Configuring a snapshot specification 
The following tasks are required to configure a snapshot specification:
Name and describe the snapshot specification, and decide if you want to perform an inventory.
- Choose target servers you want to take a snapshot of. You can choose to snapshot multiple servers or groups of servers.
- Configure your own custom rules, or choose settings from a source server to serve as the basis for the snapshot specification rules.
- Schedule the snapshot specification job to run once or on a recurring schedule.
- Set up email notifications to notify users when the snapshot specification job finishes successfully, if the job fails, or on both conditions.
- Save the snapshot specification.
If you take a snapshot of COM+ objects from a 32 bit Windows server and you attempt to remediate the results using copy to on to a Windows 64 bit server, this action might fail.
VMware ESXi servers cannot be the target of an audit or snapshot.
To configure a snapshot specification:
- In the navigation pane, select Library > By Type > Audit and Remediation.
- In the navigation pane, select Snapshot Specifications, then either Windows or UNIX.
- From the Actions menu, select New.
- In the Snapshot Specification window, enter the following information:
- Properties: Enter a name and description for the snapshot specification. Also, for certain snapshot specification rules (Discovered Software, Internet Information Server, Local Security Settings, Packages and Patches, Windows and UNIX Users and Groups), you can select the Perform Inventory option, which will capture all resources associated with the rule.
- Source: Select a source for the snapshot specification. By default, the source server for the snapshot specification will be the managed server that you chose as the source for the snapshot specification. Browse the source server for values to populate the snapshot specification’s rules. You can also choose a different source server as the basis of the snapshot specification for each rule category, or no source at all. If you choose no source, you must define your own rules, or choose to link to an audit policy in the rules section.
- Rules: Choose a rule category from the list to begin configuring your snapshot specification’s rules. Since each rule is unique and requires its own instructions, to configure specific rules see Audit and remediation rules .
If you want to use an audit policy to define the rules of your snapshot specification, click either Link Policy or Import Policy.
When you link an audit policy, the snapshot specification maintains a direct connection with the audit policy, so if any changes are made to the policy, the snapshot specification will update it with the new changes. If you import an audit policy, the snapshot specification will use all the rules defined in the policy but will not maintain a link to the audit policy. For information on how to import or link to a snapshot specification, see Ways to link and import audit policies. - Targets: Choose the Targets of the snapshot specification. These are servers or groups of servers that you want the configured snapshot specification rules to capture. To add a server or group of servers, click Add. To choose a source server to use to create the snapshot specification rules, click Select.
- Schedule: Choose to run the snapshot specification immediately, or on a recurring schedule. Choose whether you want to run it once, daily, weekly, monthly, or on a custom schedule. Parameters include:
- None: No schedule will be set. To run the snapshot specification, select the snapshot specification, right-click, and select Run snapshot specification.
- Daily: Choose this option to run the snapshot specification on a daily basis.
- Weekly: Choose a day of the week to run the snapshot specification.
- Monthly: Choose the months to run the snapshot specification.
- Custom: In the Custom Crontab string field, enter a string the indicates a time schedule.
A crontab file has five fields for specifying the day of the week, the month, the day of the month, the hour, and the minute. The following diagram shows each position in the crontab file, what the position corresponds to, and the allowed values: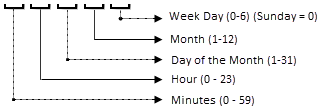
The crontab string can include serial (1,2,3,4) and range (1-5) values. Only some operating systems support the minutes format /2 or /10 for running the audit every 2 minutes or 10 minutes. An asterisk (*) denotes all values for that field, such as all months of the year. Days can be specified in two fields: month day and week day. If both days are specified, both of the values will be executed. All operating systems support comma-separated values within each field. For example:
5,10 0 10 * 1 means run an audit 12.05 and 12.10 AM every month or on the 10th and on every Monday.
For more information about crontab entry formats, consult the UNIX man pages. - Time and Duration: For each type of schedule, specify the hour and minute you want the daily schedule to start. Unless you specify an end time, the snapshot specification will keep running indefinitely. To choose an end date to end the snapshot specification schedule, select End, and from the calendar selector, choose a date. The Time Zone is set according to the time zone set in your user profile.
- Notifications: Enter the email addresses (separated by a comma or a space) of those you want to receive an email when the snapshot specification Job finishes running. You can choose to send the email notification on both success and the failure of the snapshot specification job (not the success of the audit rules). To add an email address, click Add Notification Rule.
- When you have finished configuring the snapshot specification, from the File menu, select Save.
Note To prevent runaway processes, the snapshot process will time out if it exceeds 60 minutes or if the data that is collected from a managed server exceeds 1 gigabyte (GB). If you specify that you want to collect the full contents of files in the selection criteria, the data collected might exceed the maximum size that can be successfully recorded in a snapshot.
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_sa_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





