Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Viewing snapshot results
You can view the contents of a snapshot and view detailed information about the server configurations that were recorded.
For information about remediating snapshot results, see Copying objects.
To view the contents of a snapshot:
- From one of the starting points described in Viewing snapshots , open a snapshot.
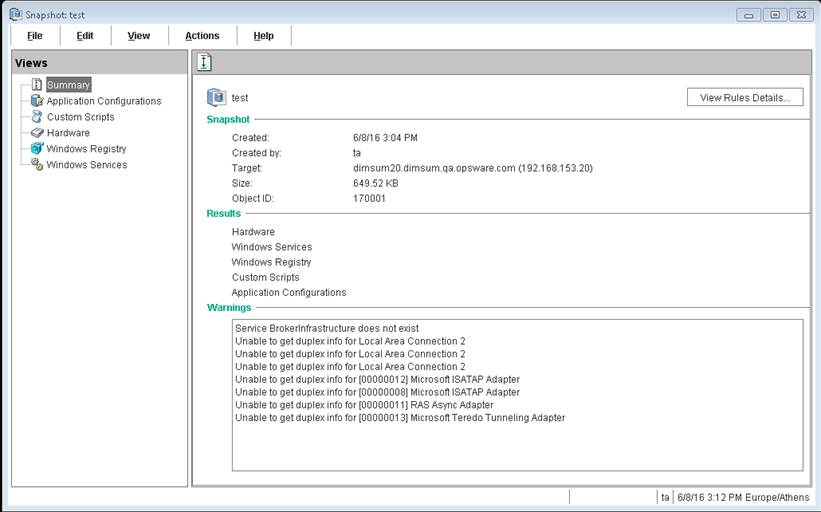
- In the Snapshot window, you can select or expand the following server objects in the Views pane:
- Summary: Displays general information about a snapshot, such as the date and time the snapshot was created and by whom, the snapshot source (name of the managed server), the size of the snapshot file, a snapshot ID number, the server that the snapshot results reference, and the IP address of that server.
ou can also click View Rules Details to see the snapshot specification which this snapshot is based on. - Compliance Library: Information relevant to the specific compliance checks configured in the snapshot specification. For more information about the types of BSA Essentials Subscription Services compliance checks available and how to configure them, see Configuring compliance checks.
- Installed Hardware:Information about the type of CPU processor and speed, cache size, memory size for SWAP and RAM, and storage devices that were recorded in the snapshot.
- Installed Patches: Displays information about the installed patches that were recorded in the snapshot, such as the patch type.
- Installed Packages: Displays information about the installed packages that were recorded in the snapshot, such as package type, package version, and release number.
- For .zip packages, the Snapshots do not show a version number, but instead displays the install path of the package on the server.
- Event Logging: Displays security, application, and system log files recorded in the snapshot.
- File System: Displays the directories, file properties, attributes, and contents of the files recorded in the snapshot.
If a file in the snapshot exceeds 2MB in file size, Audit and Remediation cannot display the file contents. - Windows Services: Displays information about the running services recorded in a snapshot, such as the name, description, startup state, startup type, and log on account.
- Windows Registry: Displays information about Windows Registry entries in the snapshot, such as the registry key, registry value, and subkey. A registry key is a directory that contains registry values, where registry values are similar to files within a directory. A subkey is similar to a subdirectory. The content area in this window excludes subkeys. Audit and Remediation supports the following Windows Registry keys: HKEY_CLASSES_ROOT, HKEY_CURRENT_CONFIG, HKEY_LOCAL_MACHINE, and HKEY_USERS.
- COM+: Displays information about Windows COM (Component Object Model) objects in the snapshot, such as the name and GUID (Globally Unique Identifier) of the object, and the path to the in-process server DLL.
- SA provides warning messages that explain how Windows COM folders were processed. The following scenarios apply:
- When you create a snapshot and select a Windows COM folder that does not contain any objects, the snapshot window displays a summary. SA displays a warning that the GUID (Globally Unique Identifier) for that folder is invalid, which means that the Windows COM folder does not contain any objects.
- When you create a snapshot specification and select a Windows COM+ object that does not exist on a target, SA displays a warning that the folder is invalid.
- When you create a snapshot and select a Windows COM+ folder that does not contain any objects, SA displays a warning that the folder is empty.
- Metabase: Displays information about IIS Metabase objects in the snapshot, such as the ID, name, path, attributes, and data of the object.
- Custom Scripts: Displays information about the custom script rule recorded in the snapshot.
- Users and Groups: Displays information about users and groups on servers, such as user name for last login, whether or not CTRL + ALT + DELETE is enabled, and so on.
- Summary: Displays general information about a snapshot, such as the date and time the snapshot was created and by whom, the snapshot source (name of the managed server), the size of the snapshot file, a snapshot ID number, the server that the snapshot results reference, and the IP address of that server.
- Click Close to close the object browser.
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_sa_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





