Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
Audit elements
An audit consists of the following elements:
- Properties: The name and description of the audit.
- Source: The source of an audit can be a server, a snapshot, or no source at all. However, some rules require a source.
Choosing a server as the source for an audit allows you to select server objects from that server as the basis of your audit.
Note If you target an ESXi server, you can only choose an ESXi server as the source.
- Choosing a snapshot as the source of an audit allows you to use the configuration values of the snapshot.
- Choosing a snapshot specification as the source allows you to audit a server against itself over time.
For example, if you took a snapshot of a server, then used that snapshot specification as the source of the audit, every time you run the audit, you can compare the original state of the server against the server’s actual configuration over time, using a recurring audit schedule. If you choose no source, you can only define your own custom values for the audit or snapshot.
- Rules: A check on a particular server object with a desired value and an optional remediation value. For example, you might check to see if this server contains a specific Windows Service, and if found, determine if the service is turned off (see Server objects).
Note For Audits created below the VMware ESXi node, only two rules (Compliance Check and Custom Script) can be used.
- Targets: The servers that the audit will check for compliance. You can choose as many servers and groups of servers as needed for an audit or snapshot.
Note Audits created below the VMware ESXi node can only target ESXi servers.
- Exceptions: Servers and specific rules that will not be checked for compliance when the audit is run.
- Schedule: You can run an audit on a one-time basis or on a recurring schedule. Audits that run on a recurring schedule appear as a single compliance column in the compliance dashboard.
- Notifications: You can send emails when the audit has finished running, and base the notification on the success, failure, or the completion of an audit job.
Configuring an audit
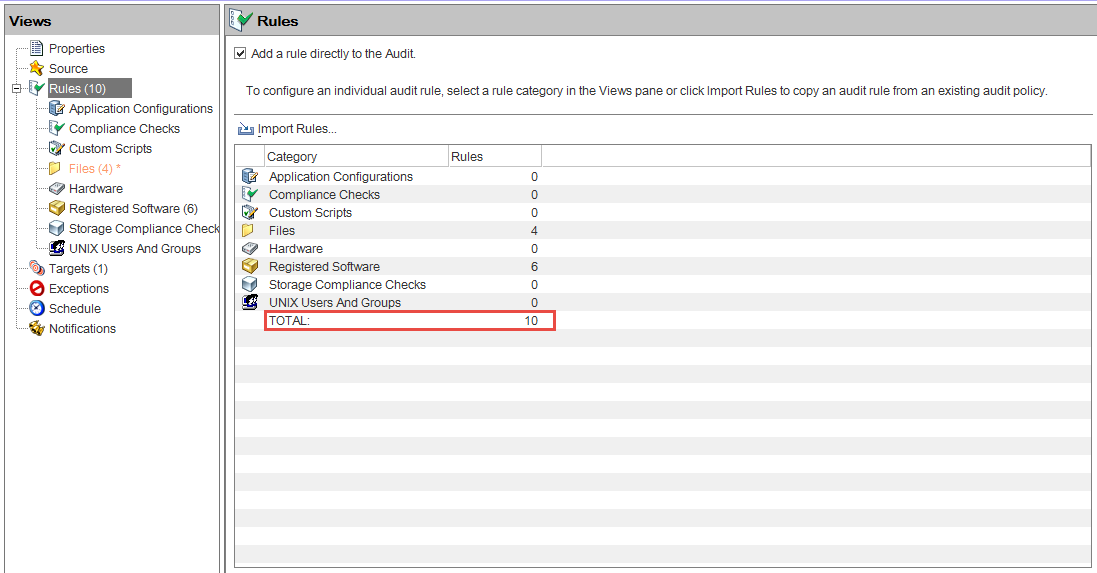
To configure an audit, select server configuration objects and then apply rules to those objects in order to define their desired configuration state. For example, the following figure shows an audit that includes 10 defined rules. These rules are used to determine whether target server configurations match the rules in the audit.
Audit browser showing objects in an audit
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_sa_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





