Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
- Audit and snapshot rules
- Configuring the application configuration rule
- Configuring the COM+ rule
- Configuring the custom scripts rule
- Configuring the discovered software rule
- Configuring the file rule
- Configuring the hardware rule
- Configuring the IIS metabase rule
- Configuring the IIS rule
- Configuring the IIS 7.0 rule
- Configuring the local security settings rule
- Configuring the registered software rule
- Configuring the Windows .NET framework configurations rule
- Configuring the Windows registry rule
- Configuring the Windows services rule
- Configuring the Windows/UNIX users and groups rule
Configuring the application configuration rule
The application configuration audit rule allows you to audit configuration file values on managed servers, to check that those files are configured the way you want them to be.
You can choose from a list of predefined application configuration templates that serve as the basis of comparison for the target configuration file you want to audit. You can also choose from custom application configurations that a user in your organization has created and made available for use in an audit, a snapshot, or an audit policy.
An application configuration in an audit models the values and structure of an application’s configuration file. This allows you to set rules that check the values in existing configuration files on managed servers.
When you choose an application configuration in an audit, snapshot, or audit policy and click View, you will see the contents of the configuration file from the source of the audit. All key-value pairs that you are able to add to the audit rule will display.
The information displayed in an Audit window depends on the source of the audit or the target for a snapshot.
- If you choose a server as the source of the audit or audit policy, the application configuration values displayed in the audit rule will be those of the configuration file on the source server, as filtered through the application configuration template.
- If you choose a snapshot as the source of the audit or audit policy, you will only be able to modify the values that were captured at the time the snapshot was taken.
- If you do not choose any source, you will not be able to configure a rule for the application configuration file.
- If you choose to configure an application configuration in a snapshot, the values of the configuration will be derived from the target server.
In an audit’s application configuration rule, you will only see values of the source configuration file that have been modelled in the application configuration. If the application configuration is customized and has no custom attributes defined (but the value exists in the source configuration file), you will not see it in the audit or audit policy.
After you view the contents of the source application configuration file, you can define your rules by selecting values from the source file and building rules that will be used to check against the target configurations. You can also define remediation values in the event that the audit finds differences between the rules and the target configuration file values.
Creating an application configuration rule
To understand how to configure an application configuration rule, it is helpful to look at an example.
Example: Your goal is to create an audit rule for a UNIX hosts file (/etc/hosts) and then audit a group of servers’ /etc/hosts files to make sure they contain the correct values. You know that the UNIX hosts file on a particular golden server represents the ideal state of hosts file configuration that you would like other servers to conform to. You can choose that golden server as the source for your audit and borrow the values from that file to construct the rule for the audit. After you create the rule and save the audit, you can run the audit against a group of servers to see if their /etc/hosts files are configured correctly (according to the audit rule).
In this example, the equals (=) operator is used. Valid operators for an application configuration rule are:
= (equals), <> (does not equal), < (less than), <= (less than or equal to), > (greater than), >= (greater than or equal to), Contain, Does not contain, Match RE, and Does not match RE.
To create an application configuration rule:
- Create an audit from any one of the methods for creating an audit described in Creating an audit . If you want to create this rule for a snapshot specification, see Creating a snapshot specification .
- Select an Audit Source: Server, Snapshot, Snapshot Specification, or No Source.
The source selected for the audit will determine what types of rules, if any, you can create for an application configuration. You must choose a source or you will not be able to configure the application configuration rule. - In the Audit window, in the Views pane, select Rules > Application Configurations.
- In the content pane, click
 to access all available configuration templates.
to access all available configuration templates. - In the Select Configuration Templates window, select one or more templates you would like to add to the audit rule and then click OK.
- Select the template you want to configure. Its contents appear in the template editor.
- Click View to see the contents of the configuration file in the File View tab.
If you cannot see the contents of the configuration file, enter the correct path in the Filename section.
Example: If you view a UNIX hosts file, you would see information similar to the example in the following figure. You can see the contents and the IP address/host name pairs from the source hosts file (highlighted in blue text).
Application Configuration Audit Rule for Hosts File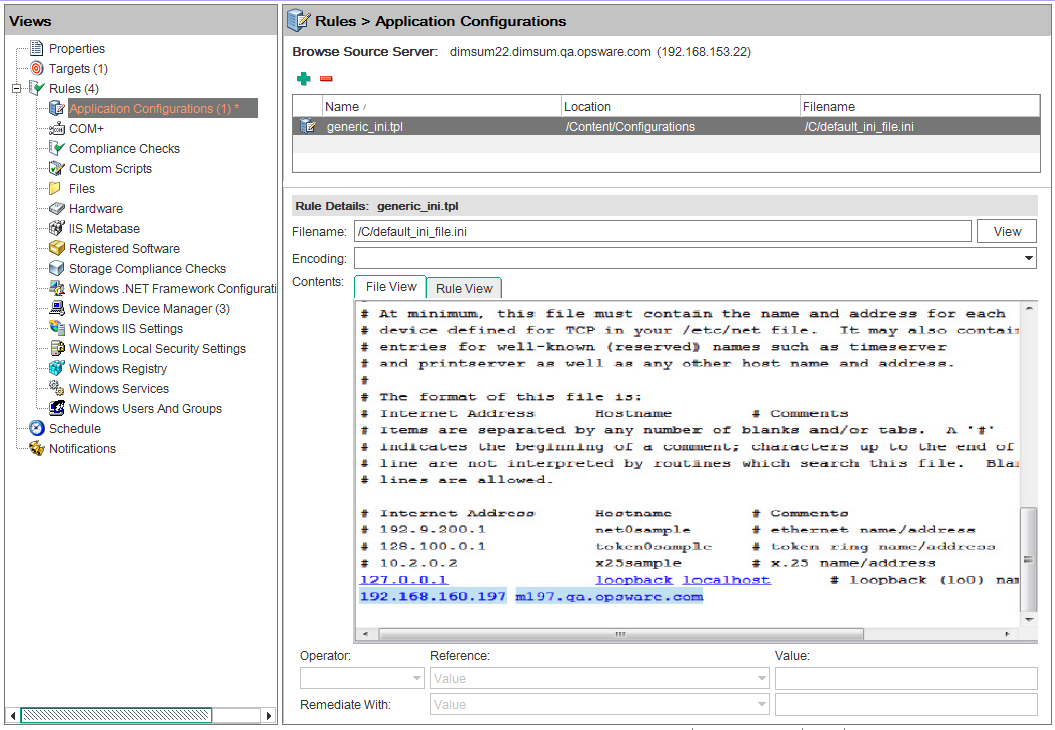
- To create an audit rule for this configuration file, choose a key-value pair from the hosts file on the source server (the server you choose as the source for the audit).
- To create this rule, select an IP addresses in the File View tab area. This shows the contents of the file obtained from the source server. In the example above, you can select an IP address such as 127.0.0.1. After you select the IP address, the element becomes highlighted in blue. Blue text means that the element is ready to have a rule created from it.
After you have selected the IP address in the contents area, the value in the Operator field is empty. This means that an operator has not yet been added to the rule. To add the value to the rule, you can either double-click it or enter the following parameters in the rule expression area below the contents:- Operator: Choose = (equals). When you change the operator to =, the equals operator immediately becomes added to the rule. If you change the operator back to no selection, the operator is immediately removed from the rule.
- Reference: Choose Value.
- Value: Enter 127.0.0.1.
- Remediate With: Enter 127.0.0.1.
This expresses that you want to look for an IP address with the value of 127.0.0.1. If this is not found, the remediation should be 127.0.0.1, so you can add this to any host files on the target servers that do not contain this IP address.
- Select a host name in the File View tab area. The initial IP address you selected in the previous step has turned green. Green text means that the next rule parameter you set will be paired with the IP address you previously selected.
- In the Rule section, set the following parameters:
- Operator: Choose = (equals).
- Reference: Choose Value. If you choose a custom attribute for the rule definition, this custom attribute must also exist on the target servers or the audit for this rule will fail.
- Value: Choose host.
- Remediate With: Choose host. This adds the final part of the rule that will check the target server for the key-value pair of the IP address 127.0.0.1 matched with host.
-
Select the Rules View tab. The rule will be expressed as:
“Check that there is an entry where IP address is equal to value 127.0.0.1 and Hostnames contains an entry equal to value host.”
This rule is what will be used to audit the hosts file on the target server or snapshot specification.Note
The IP address and hostname are key-value pairs, so you must always provide an IP address and a Hostname together. - To configure more application configuration rules, select more application configurations from the Available for Audit section.
- To finish configuring the audit, define other rules and set the target servers, schedule, and notification for the audit.
- Save the audit.
- To run the audit, from the Actions menu, select Run audit. See Running an audit for more information.
Application configuration audit rule
When you first view an application configuration, all elements that can be used to build an audit rule will appear in blue underlined text. After you start selecting and building rules, then the colors will change. The following table describes the color scheme used for configuring application configuration audit rules.
|
Text Color |
Description |
|---|---|
|
Blue Underlined |
All elements in the source configuration file that can be used in a rule. |
|
Highlighted Dark Blue |
A selected element that does not have a rule associated with it. |
|
Highlighted Light Blue |
An element that has been added to a rule. |
|
Highlighted Medium blue |
A selected element that has a rule associated with it. |
|
Green |
An element that is a primary key, is related to the currently selected element, and is used in the same rule as the currently selected element. If the currently selected element is given a comparison value (=, contains, matches...), the other elements with green text will automatically be given a comparison value of =, such as:
If localhost is selected, There is an entry where ip is equal to |
|
Bold |
A primary key. |
|
Italicized |
Custom attribute or SA attribute. |
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to hpe_sa_docs@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:





