Searching the Help
To search for information in the Help, type a word or phrase in the Search box. When you enter a group of words, OR is inferred. You can use Boolean operators to refine your search.
Results returned are case insensitive. However, results ranking takes case into account and assigns higher scores to case matches. Therefore, a search for "cats" followed by a search for "Cats" would return the same number of Help topics, but the order in which the topics are listed would be different.
| Search for | Example | Results |
|---|---|---|
| A single word | cat
|
Topics that contain the word "cat". You will also find its grammatical variations, such as "cats". |
|
A phrase. You can specify that the search results contain a specific phrase. |
"cat food" (quotation marks) |
Topics that contain the literal phrase "cat food" and all its grammatical variations. Without the quotation marks, the query is equivalent to specifying an OR operator, which finds topics with one of the individual words instead of the phrase. |
| Search for | Operator | Example |
|---|---|---|
|
Two or more words in the same topic |
|
|
| Either word in a topic |
|
|
| Topics that do not contain a specific word or phrase |
|
|
| Topics that contain one string and do not contain another | ^ (caret) |
cat ^ mouse
|
| A combination of search types | ( ) parentheses |
|
- System Administrator
- Logon
- Splash Screen
- Launch or Stop the Business Analytics Application
- Configure CAC
- Licenses
- About Users, Roles, Resources, Permissions, LDAP, and Dimension Permissions
- Users and Roles - User Management
- Users and Roles - Role Management
- Users and Roles - Resource Management
- Users and Roles - LDAP Management
- LDAP in BusinessObjects
- Users and Roles - Dimension Permissions
- Settings
- Settings - Data Warehouse
- Settings - Foundation
- Settings - Single Sign On
- Settings - Pages
- Settings - Website
- Settings - Dashboard Settings
- Settings - Engine Settings
- Settings - Score Thresholds
- Settings - BA Settings
- Apache Web Server
- Security Recommendations
- LW-SSO
- Cryptography
- Set Up Java
- Localization and Globalization
- Xcelsius Reports
- Browsers and BOE Reports
- Notifications - Entity Report
- External Tools
- Migrate from a Development or Test Environment to Production
- Vertica Back Up
- Business Analytics Back Up
- Disaster and Recovery
The LDAP Management page enables you to add and edit users and groups, as well as add and edit their details.
Users can be managed using either of the following, but not both:
- Enterprise Users: Users are created and managed in IT Business Analytics.
- LDAP Users: Users are created and managed on your LDAP server which is connected to IT Business Analytics. For details, see Users and Roles - LDAP Management.
The Administrator uses the Admin tab to define users that have roles, roles that contain a set of permissions that may contain resources. It is recommended to create resources and attach them to permissions first in the user management process. For details, see Users and Roles - Role Management.
Select ADMIN> Users and Roles > LDAP Management to access the LDAP Management page.
 Users and authentication when working with SAP BusinessObjects and LDAP or without
Users and authentication when working with SAP BusinessObjects and LDAP or without
The users and authentication when working with or without SAP BusinessObjects and LDAP is as follows:
| Operation | Working without SAP BusinessObjects and without LDAP |
Working with SAP BusinessObjects and without LDAP |
Working with SAP BusinessObjects and with LDAP |
|---|---|---|---|
| Manage users (create, remove, update) | In ITBA, in ADMIN > Users and Roles. |
Users are created in ITBA, in ADMIN > Users and Roles Users created in ITBA are automatically transferred to SAP BusinessObjects. If a user is created in SAP BusinessObjects, it does not appear in the list of users in ITBA. |
Users are created in LDAP. If LDAP configures successfully, ITBA loads all the user information from LDAP automatically . |
| Passwords |
Passwords can be changed in the User Details pane of the User Management page in ITBA. Click Edit Details to change a user's password. |
Passwords can be changed in the User Details pane of the User Management page in ITBA. Click Edit Details to change a user's password. A password created in ITBA is automatically transferred to SAP BusinessObjects for the relevant user. |
Passwords are created and stored in LDAP. |
| Roles, permissions, and groups | In ITBA, in ADMIN > Users and Roles. | In ITBA, in ADMIN > Users and Roles. | In ITBA, in ADMIN > Users and Roles. |
Note
- The format of the LDAP directory must be either Microsoft Active Directory or Sun ONE Directory. It cannot be an arbitrary directory structure.
-
Active Directory provides two password options:
-
Option 1 - You must change the password at the next log on.
-
Option 2 - Password never expires.
IT Business Analytics only supports the second option. If you want to use the first option, you must log on to another system (not IT Business Analytics) the first time to change the password, and then use the new password to log on IT Business Analytics.
-
- When a user is added to LDAP, it is displayed in the Users and Groups tree after you log on to IT Business Analytics.
-
When working with LDAP, you must make sure that LDAP is connected to ITBA and to SAP BusinessObjects. For details, see Create a connection.
- ITBA only supports the LDAP tab with Active Directory as a server type on that tab. Active Directory authentication via the active directory tab is not supported.
- We recommend to use LDAP for secure passwords and better password validation.
 Searches for LDAP user groups
Searches for LDAP user groups
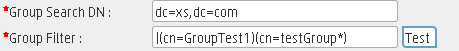
The root group filter specifies the groups that will be listed as the root group in ITBA.The group filter specifies the child groups that will be listed under the root groups.
The group scope should include the root groups and some of the child groups listed under the root group.
If, for example,you have the following configuration in the LDAP server:
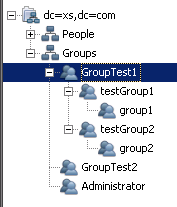
And you want to display the below group in ITBA:
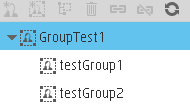
-
If you click Test for the Root Group Filter, you only need to specify the Root Group Search DN and the Root Group Filter values.
The Root Group Search DN is the starting search node and dc=hpxs,dc=com points to the root node. The Root Group Filter is used to locate the specific node: GroupTest1.
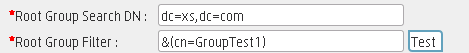
-
Then the Group Search DN must include the root group value specified in the Root Group Search DN and the relevant child groups under the root group.
In our example, the Group Filter should contain the root group: GroupTest1 and the child groups: testGroup1 and testGroup2.
 LDAP and the Licenses
LDAP and the Licenses
LDAP support the ITBA license set up. For details, see Licenses.
You create and manage users on your LDAP server which is connected to ITBA. The ITBA Administrator uses the ADMIN tab to define users that have roles, roles that contain a set of permissions that may contain resources. It is recommended to create resources and attach them to permissions first in the user management process. For details, see Users and Roles - Role Management.
 Configure LDAP to work with Dimension Level Permission
Configure LDAP to work with Dimension Level Permission
Note Make sure that you perform the update below before you configure LDAP.
- Click ADMIN> Users and Roles > LDAP Management to access the LDAP Management page.
-
Fill in LDAP configuration information and then fill in the relevant information in the Dimension Permission Group for New Entities, and Dimension Permission Group for Unassigned Entities fields.
- Click Save.
Note
- If you have already set up Dimension Level Permissions and you start working with LDAP, note that all the existing DLPs are automatically set to dlp.default.group.permission. You must first perform the operation above and then click ADMIN > Users and Roles > LDAP Management and set up and enable LDAP.
- If you are working with DLP and LDAP and you want to stop working with LDAP, note that the existing DLPs are automatically set to dlp.default.group.permission . You must then perform the operation above and then click ADMIN > Users and Roles > LDAP Management and disable LDAP.
 Check if LDAP mode is enabled
Check if LDAP mode is enabled
- In theITBA application, click ADMIN > Users and Roles > LDAP Management.
-
If the LDAP configuration has already been updated, a Warning message: You have updated the LDAP configuration. Restart the server. is displayed. Restart the server.
If the configuration is not complete, enter the relevant values in the fields, and click Save. Then restart the server.
 Create a connection
Create a connection
Note
Configure LDAP to connect separately with:
- the IT Business Analytics server.
- optionally, the SAP BusinessObjects Enterprise server.
You create a connection and verify that the server information is correct.
- After you enter the server information in the LDAP Management page, click Next.
-
If the connection is created successfully, the LDAP configuration page opens. You can then:
- Enter the information in the remaining fields
- Click Back to input different information in the server information fields.
-
When you check the SSL mode, the ITBA server attempts to connect with the LDAP server.
If the server cannot perform the connection, the following error message is issued:
The BA server cannot connect to the LDAP server.
Make sure all the relevant certificates are imported.
After the relevant certificates are imported, restart the BA server.
In such a case, make sure that the relevant certificates are imported. After the import of the relevant certificates completes, restart the server.
-
If you need to import a certificate from a third-party Certificate Authority (CA) or if you need to generate a self-certificate:
- Make sure the certificate is supported by the LDAP server and placed in the correct keystore.
- Navigate to the ITBA server .
- Open CMD and import the certificate using the following command:
$HPBA_Home/jdk/bin/keytool -import -trustcacerts -alias hpxsldap-ssl -file <Certificate File Path> -keystore $HPBA_Home/jdk/jre/lib/security/cacerts
- At the Enter keystore password: prompt, enter changeit.
- When asked to trust this certificate, enter y.
-
Restart the ITBA server.
 Test the input fields
Test the input fields
After verifying that the server information is correct and enables the connection to the server, test users with the Admin role.
-
After you enter the base and filter values for the root group, group, or user, click the relevant Test button to see whether there are results or not.
- Root group info should only show the root group.
- Group info should only show the group tree.
- User info should show all users.
For additional information, see Searches for LDAP user groups.
-
You can also select some of the LDAP users. These users will be assigned the Admin role, in the ITBA application, to these users.
 Save and disable an LDAP configuration
Save and disable an LDAP configuration
After you have saved the LDAP configuration, the status of the LDAP changes to Enabled 
After the LDAP Admin disables the LDAP mode:
- The users and groups used by ITBA are loaded from the ITBA local database and not from the LDAP server anymore.
-
The LDAP Admin must create a new ITBA Admin user.
If the ITBA Administrator name is the same as the BOE Administrator name (BOE Administrator was created during the installation of ITBA), then the BOE Administrator password is the same as the ITBA Admin password.
 Configure LDAP
Configure LDAP
- In the ITBA application, click ADMIN > Users and Roles > LDAP Management.
- In the LDAP Management page, enter the server information. Click Next.
- Enter all the DN and filter fields, and click Test in turn for the Test Root Group, the Test group, the Test Users, and then click ... to select the users.
-
Click ... to select Dimension Permission Group for New Entities and select Dimension Permission Group for Unassigned Entities.
- Click Save. A warning to restart the server is issued. Click OK to do so.
 Configure BOE to work with LDAP
Configure BOE to work with LDAP
Make sure you use the LDAP Authentication option:
-
Log on to the Central Management Console as an administrator.
-
Click Authentication, then click the LDAP tab.
-
Click Start LDAP Configuration Wizard.
-
In the Add LDAP Host (hostname: port) field, type your host and port information.
-
Click Add.
-
Click Next.
-
In the LDAP Server Type drop-down list, select your LDAP server, and click Next. This is where you select the type of server you are using: Sun One or Active Directory.
- If you select Active Directory, click Show Attribute Mappings.
- In the Default User Search Attribute field, enter sAMAccountName.
- In the User Name field, enter sAMAccountName.
-
In the Base LDAP Distinguished Name field, type the distinguished name, and click Next.
-
Type the LDAP host credentials:
-
LDAP Server Administration Credentials: Enter the name and password for a user account that has rights to administer your LDAP server.
-
LDAP Referral Credentials: Enter the same name and password you entered for LDAP Server Administration Credentials.
-
-
In the Maximum Referral Hops field, type the number of referral hops to limit forwarding the credential request. If you set this field to zero, no referral hops are allowed.
-
Click Next.
-
In the Type of SSL authentication drop-down list, select Basic (no SSL) and click Next.
-
In the Authentication drop-down list, select Basic (no SSO) and click Next.
-
Select the following LDAP options:
-
Create a new account for every added LDAP alias
-
Create new aliases when Alias Update occurs
-
New users are created as named users
-
-
Click Next.
-
Click Finish.
 Set up so ITBA users can use and view BOE reports in the ITBA application
Set up so ITBA users can use and view BOE reports in the ITBA application
To set up so ITBA users can use and view BOE reports in the ITBA application, the Admin must join a LDAP group to the group in the BOE that has permission to see the Reports. Then all the users in this LDAP group will have permission to use and see the BOE reports.
-
Log on to the Central Management Console as an administrator.
Click Authentication, then click the LDAP tab.
- Locate the Add LDAP group (by cn or dn) field in the LDAP screen. Enter the Group Name configured in the LDAP Server, and click Add. Scroll downwards and click Update.
- Navigate to Home > Group List, right-click the group added in the previous and select Member Of. The Member Of dialog box opens.
- Click Join Group.
- Navigate to Group List, select a group that has authority to view the BO reports, and then click the right arrow (>) to add it to the Destination Group.
- Click OK.
 Configure ITBA to work with LDAP - Advanced LDAP Configuration
Configure ITBA to work with LDAP - Advanced LDAP Configuration
Note Use this advanced procedure only if the wizard described in the UI Description section is not sufficient for your purposes. For details, see .
To configure ITBA to work with LDAP:
-
Database changes. In the Management database, in the SETTINGS_MANAGEMENT table create a new record with:
- context=foundation
- name=fnd.uum.type
- value=ldap
-
external-ldap.properties. Define groups and users in LDAP. In the
$HPBA_Home/glassfish/glassfish/domains/BTOA/config/conf/external-ldap.propertiesfile, enter the relevant parameter values or use the provided default:Parameter Description ldapversion 3 - LDAP V3.
2 - LDAP V2.
Default: 3
Example: ldapVersion = 3
ldapHost The name of the machine running the LDAP server.
Default: localhost
Example: ldapHost = ldap.hp.com
ldapPort The port number of the machine running the LDAP server.
Default: 389
Example: ldapPort = 636
useAdministrator true.The LDAPConnection is created with the provided Administrator username and password.
false. The LDAPConnection is created without username/password.
Default: false
Note If you work with LDAP V2, the LDAP connection must be created with the administrator username and password, so you must set useAdministrator = true.
Example: useAdministrator = true
ldapAdministrator The Administrator logon name used for creating the initial LDAP connection. The parameter is ignored if useAdministrator=false.
Default:CN=Administrator
Example: ldapAdministrator = CN=Administrator
ldapAdministrator
PasswordThe Administrator logon password used for creating initial LDAPConnection. The parameter is ignored if useAdministrator=false.
Default: <empty_value>
enableSSL true - If the customer requires the SSL connection to LDAP. The SSL connection to the port defined in ldapPort property is attempted.
false - Default.
Default: false
Example: enableSSL = false
baseDistinguish
NameDelimiterThe regular expression used to separate names in parameters that accept a number of different names, like usersBase, groupsBase, and more.
Default: \\s*;\\s*
Example: baseDistinguishNameDelimiter = \\s*;\\s*
scopeDelimiter The regular expression used to separate search scope string (SCOPE_SUB, SCOPE_ONE, SCOPE_BASE) in parameters that accept a number of different search scopes, like usersScope, groupsScope, and more.
Default: \\s*,\\s*
Example: scopeDelimiter = \\s*,\\s*
usersBase The base DN (distinguished name) for users search.
Default: dc=example, dc=com
Example: usersBase = ou=People,dc=hp, dc=com
usersScope SCOPE_SUB - The user search is a recursive search in the tree defined in usersBase property.
SCOPE_ONE - The user search is performed across one level (direct children only) in the tree defined in usersBase property.
SCOPE_BASE - The user search returns one entry maximum, as indicated in the usersBase property.
Default: SCOPE_SUB
Example: usersScope = SCOPE_SUB, SCOPE_SUB
usersFilter The search filter, indicating what instances should be returned from the LDAP search.
Default: (&(uid=*)(objectclass=inetOrgPerson))
Example: usersFilter = (&(uid=*)(objectclass=inetOrgPerson))
enableNestedGroups true - The users and groups search works recursively and looks for all users in subgroups returned by the groups search filter.
false - The users and groups search looks for users in the results by the groups search filter (it does not include subgroups.
Default: true
Example: enableNestedGroups = true
maximalAllowedGroups
HierarchyDepthThe maximum allowed groups hierarchy depth.
This parameter is relevant only if enableNestedGroups=true.
A negative value allows unlimited depth.
Default: 10
Example: maximalAllowedGroupsHierarchyDepth = 10
enableDynamicGroups true- The search executes a URL query to bring all users for dynamic groups.
false - The dynamic groups URLs are ignored by the URL query.
Default: false
Example: enableDynamicGroups = true
groupsBase. The base dn (distinguished name) for groups search.
Default: <userBase value>
Example: groupsBase = ou=Groups,dc=hp, dc=com
groupsScope SCOPE_SUB - The group search is a recursive search in the tree defined in groupsBase property.
SCOPE_ONE - The group search is performed across one level (direct children only) in the tree defined in groupsBase property.
SCOPE_BASE - The group search returns one entry maximum, as indicated in the groupsBase property.
Default:SCOPE_SUB
Example: groupsScope = SCOPE_SUB
groupsFilter The search filter, indicating what instances should be returned from the LDAP search.
Default:
(|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole))
Example: groupsFilter =
(|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\ (objectclass=accessGroup)(objectclass=accessRole))rootGroupsBase The base dn (distinguished name) for root groups search.
Default:<usersBase value>
Example: rootGroupsBase = ou=People,dc=hp, dc=com
groupsScope SCOPE_SUB - The root group search is a recursive search in the tree defined in groupsBase property.
SCOPE_ONE - The root group search is performed across one level (direct children only) in the tree defined in groupsBase property.
SCOPE_BASE - The root group search returns one entry maximum, as indicated in the groupsBase property.
Default:SCOPE_SUB
Example: rootGroupsScope = SCOPE_SUB
rootGroupsFilter The search filter, indicating what instances should be returned from the LDAP search.
Default:
(|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole))
Example: rootGroupsFilter =
(|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\(objectclass=accessGroup)(objectclass=accessRole))rolesBase The base dn (distinguished name) for roles search.
Default: <usersBase value>
Example: rolesBase = ou=People,dc=hp, dc=com
rolesScope SCOPE_SUB - Theroles search is a recursive search in the tree defined in rolesBase property.
SCOPE_ONE - The roles search is performed across one level (direct children only) in the tree defined in rolesBase property.
SCOPE_BASE - The roles search returns one entry maximum, as indicated in the rolesBase property.
Default: SCOPE_SUB
Example: rolesScope = SCOPE_SUB
rolesFilter The search filter, indicating what instances should be returned from the LDAP search.
Default:
(|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole))
Example: rolesFilter =
(|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\(objectclass=accessGroup)(objectclass=accessRole))rootRolesBase The base dn (distinguished name) for root roles search.
Default:<usersBase value>
Example: rootRolesBase = ou=People,dc=hp, dc=com
rootRolesScope SCOPE_SUB - The root groups search is a recursive search in the tree defined in groupsBase property.
SCOPE_ONE - The root groups search is performed across one level (direct children only) in the tree defined in groupsBase property.
SCOPE_BASE - The root groups search returns one entry maximum, as indicated in the groupsBase property.
Default: SCOPE_SUB
Example: rootRolesScope = SCOPE_SUB
rootRolesFilter The search filter, indicating what instances should be returned from the LDAP search.
Default:
(|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole))
Example: rootRolesFilter =
(|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\(objectclass=accessGroup)(objectclass=accessRole))enableDynamicRoles true- The search executes a URL query to bring all users for dynamic groups.
false - The dynamic groups URLs are ignored by the URL query.
Default: false
Example: enableDynamicRoles = true
enableNestedRoles true- The users and groups search are recursive and looks for all users in subgroups returned by the group search filter.
false - The users and groups search looks for users in the results by the group search filter (it does not include subgroups.
Default: true
Example: enableNestedRoles = true
maximalAllowedRoles
HierarchyDepthThe maximum allowed groups hierarchy depth.
This parameter is relevant only if enableNestedGroups=true.
A negative value allows unlimited depth.
Default: 10
Example:
maximalAllowedRolesHierarchyDepth = 10SIZELIMIT This variable limits the total number of results, returned from LDAP by one search.
0 - no limit.
LDAP may be (and usually is) configured to limit this number for non-administrators. In this case, the application may receive less results then expected. The usual limit is 1000.
Default: 0
Example: SIZELIMIT = 0
TIMELIMIT This variable limits the total number of times spent by LDAP on one search.
0 - no limit.
LDAP may be (and usually is) configured to limit this number for non-administrators. In this case, the application may receive less results then expected.
Default: 0
Example: TIMELIMIT = 0
REFERRALS Some objects in LDAP may be just referrals to another LDAP that contains the required information.
true - The search follows the references automatically, till the number indicated by the REFERRALS_HOP_LIMIT property.
false - The search may not return all required results. This also happens when the number of HOPs is exceeded.
Default: true
Example: REFERRALS = false
REFERRALS_HOP_LIMIT The number of times the referrals are followed, until the exception is thrown terminating the search.
Default: 10
Example: REFERRALS_HOP_LIMIT = 10
ldapReferralHost Referrals credentials (if needed).
If ldapHost is defined as:
- An IP, set ldapReferralHost as an IP.
- A DNS name, set ldapReferralHost as a DNS name.
- A string, for example LDAP host = ldap://test.net, port=389, set "ldapReferralHost = test.net", and set "ldapReferralPort = 389".
Example: ldapReferralHost = test.net
ldapReferralPort LDAP connections are to port 389, or 636 for secure connections. This searches the Active Directory (AD) Domain.
For Active Directory: Use an LDAP search port and not a Global Catalog search port.
Default: 389 (636 for secure connections)
Tip It is not recommended to use the Global Catalog LDAP connections: 3268 and 3269 (secure) that perform Forest wide searches (multiple domain searches).
Example: ldapReferralPort = 389
ldapReferralUser The username (used for creating referral LDAP Connection).
Default: cn=Directory Manager
Example: ldapReferralUser cn=Directory Manager
ldapReferralPassword The password (used for creating referral LDAPConnection).
Default: <empty password>
Example: ldapReferralPassword = mercurypw
baseReferralDelimiter The regular expression used to separate values in above referral parameters.
Example: baseReferralDelimiter = \\s*;\\s*
ldapAuthNUsers
ReferralBaseThe base for authentication with users from referral.
Specify only if you want to authenticate with users from the referred LDAP.
Example: ldapAuthNUsersReferralBase = dc=test,dc=net
BATCHSIZE The minimal size of chunks that must be received before the result may be processed.
This parameter influences only the efficiency of lazy reading of the search results.
Default: 1
Example: BATCHSIZE = 1
MAXBACKLOG The size of queue, waiting for BATCH results, if BATCHSIZE is not 0.
This parameter influences only the efficiency of lazy reading of the search results.
Default: 1000
Example: MAXBACKLOG = 1000
attributeValuesDelimiter The regular expression used to separate attribute names in parameters that accept a number of different attribute names, as usersObjectClass, usersUniqueIDAttribute, and more.
Default: \\s*;\\s*
Example: attributeValuesDelimiter = \\s*;\\s*
usersObjectClass The object class used for storing the users information.
inetOrgPerson - for SunOne Directory.
user - for Microsoft Active Directory.
Default: inetOrgPerson
Example: usersObjectClass = inetOrgPerson
usersUniqueIDAttribute The unique ID attribute. This attribute should store the actual login name of the user. The dn search and authentication functions suppose that this attribute is unique.
uid - for SunOne Directory.
sAMAccountName - for Microsoft Active Directory.
Default: uid
Example: usersObjectClass = inetOrgPerson
usersDisplayName
AttributeThe attribute used to store the user's display name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
cn - for Microsoft Active Directory.
Default: cn
Example: usersDisplayNameAttribute = cn
usersLoginNameAttribute
usersFirstNameAttribute
usersLastNameAttribute
usersEmailAttribute
usersPreferredLanguage
AttributeusersPreferredLocation
AttributeusersTimeZoneAttribute
usersDateFormatAttribute
usersNumberFormatAttribute
usersWorkWeekAttribute
usersTenantIDAttribute
The default attributes that are supported ad hoc in the BSFPrincipal object.
Default:Defaults are given for the SunOne directory server.
usersLoginNameAttribute = uid
usersFirstNameAttribute = givenName
usersLastNameAttribute = sn
usersEmailAttribute = mail
usersPreferredLanguageAttribute = preferredLanguage
usersPreferredLocationAttribute = l
usersTimeZoneAttribute = undefinedAttribute
usersDateFormatAttribute = undefinedAttribute
usersNumberFormatAttribute = undefinedAttribute
usersWorkWeekAttribute = undefinedAttribute
usersTenantIDAttribute = undefinedAttribute
groupsObjectClass The object class used for storing the static group information.
groupOfUniqueNames - for SunOne Directory.
group - for Microsoft Active Directory.
Default: groupOfUniqueNames
Example: groupsObjectClass = groupOfUniqueNames
groupsMembersAttribute Attribute used to store the group's member information.
uniqueMember - for SunOne Directory.
member - for Microsoft Active Directory.
Default: uniqueMember
Example:
groupsMembersAttribute = uniqueMember, membergroupsNameAttribute Attribute used to store the group name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
cn - for Microsoft Active Directory.
Default: cn
Example: groupsNameAttribute = cn
groupsDisplayName
AttributeAttribute used to store the group's display name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
cn - for Microsoft Active Directory.
Default: cn
Example: groupsDisplayNameAttribute = cn
groupsDescription
AttributeAttribute used to store the group's description. The uniqueness of this attribute is not required.
description - for SunOne Directory.
description - for Microsoft Active Directory.
Default: description
Example: groupsDescriptionAttribute = description
dynamicGroupsClass The object class used for storing the dynamic groups information.
groupOfUrls - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: groupOfUrls
Example: dynamicGroupsClass = groupOfUrls
dynamicGroupsMember
AttributeAttribute used to store the search URL, defining the members of the dynamic group.
memberUrl - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: memberUrl
Example:
dynamicGroupsMemberAttribute = memberUrldynamicGroupsName
AttributeAttribute used to store the dynamic group name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: cn
Example: dynamicGroupsNameAttribute = cn
dynamicGroupsDisplay
NameAttributeAttribute used to store the dynamic group's display name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: cn
Example: dynamicGroupsDisplayNameAttribute = cn
dynamicGroups
DescriptionAttributeParameter used to store the dynamic group's description. The uniqueness of this attribute is not required.
description - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: description
Example:
dynamicGroupsDescriptionAttribute = descriptionuseBottomUpAlgorithm
ForFindParent
GroupsOfUserPlainThis parameter is used for optimization of function FindParentGroupsOfUserPlain.
true - The algorithm should be the false, but for some LDAP Configurations it is possible that value false will be better.
false - Change to false only if you experience performance issues with this specific function.
Default:true
Example:
useBottomUpAlgorithmForFindParent
GroupsOfUserPlain = truenotAGroupAttribute When the search group is from LDAP, if the DN (distinguished name) includes these values, it is filtered and not treated as a group type.
Default:uid, samaccountname
Example: notAGroupAttribute = uid, samaccountname
rolesObjectClass Object class used for storing the static role information.
Default:groupOfUniqueNames
Example: rolesObjectClass = groupOfUniqueNames, groupOfNames
rolesMembersAttribute Attribute used to store the role's member information.
uniqueMember - for SunOne Directory.
member - for Microsoft Active Directory.
Default:uniqueMember
Example: rolesMembersAttribute = uniqueMember, member
rolesNameAttribute Attribute used to store the role name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
cn - for Microsoft Active Directory.
Default: cn
Example: rolesNameAttribute = cn
rolesDisplayName
AttributeAttribute used to store the role display name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
cn - for Microsoft Active Directory.
Default: cn
Example: rolesDisplayNameAttribute = cn
rolesDescriptionAttribute Attribute used to store the role description. The uniqueness of this attribute is not required.
description - for SunOne Directory.
description - for Microsoft Active Directory.
Default: description
Example: rolesDescriptionAttribute = description
dynamicRolesClass Object class used for storing the dynamic roles information.
groupOfUrls - for SunOne Directory.
Microsoft Active Directory is not supported.
Default: groupOfUrls
Example: dynamicRolesClass = groupOfUrls
dynamicRolesMember
AttributeAttribute used to store the search URL, defining the members of the dynamic role.
memberUrl - for SunOne Directory.
Microsoft Active Directory is not supported.
Default:memberUrl
Example: dynamicRolesMemberAttribute = memberUrl
dynamicRolesName
AttributeAttribute used to store the dynamic role name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
Microsoft Active Directory is not supported.
Default:cn
Example: dynamicRolesNameAttribute = cn
dynamicRolesDisplay
NameAttributeAttribute used to store the dynamic role display name. The uniqueness of this attribute is not required.
cn - for SunOne Directory.
Microsoft Active Directory is not supported.
Default:cn
Example: dynamicRolesDisplayNameAttribute = cn
dynamicRoles
DescriptionAttributeParameter used to store the dynamic role description. The uniqueness of this attribute is not required.
description - for SunOne Directory.
Microsoft Active Directory is not supported.
Default:description
Example: dynamicRolesDescriptionAttribute = description
notARoleAttribute When the search group is from LDAP, if the DN (distinguished name) includes these values, it is filtered and not treated as a role type.
Default: uid, samaccountname
Example: notARoleAttribute = uid, samaccountname
vlvUsersBase Base dn (distinguished name) for users search for Virtual List View (VLV) API.
Default:dc=example, dc=com
Example: vlvUsersBase = ou=People,dc=hp, dc=com
vlvUsersScope SCOPE_SUB - The users search for Virtual List View (VLV) API is a recursive search in the tree defined in usersBase property.
SCOPE_ONE - The users search for Virtual List View (VLV) API is performed across one level (direct children only) in the tree defined in usersBase property.
SCOPE_BASE - The users search for Virtual List View (VLV) API returns one entry maximum, as indicated in the usersBase property.
Default:SCOPE_SUB
Example: vlvUsersScope = SCOPE_SUB
vlvUsersFilter Search filter, indicating what instances should be returned from the LDAP search for Virtual List View (VLV) API.
Default:(&(uid=*)(objectclass=inetOrgPerson))
Example: vlvUsersFilter = (&(uid=*)(objectclass=inetOrgPerson))
vlvGroupsBase Base dn (distinguished name) for groups search for Virtual List View (VLV) API.
Default:dc=example, dc=com
Example: vlvGroupsBase = ou=Groups, dc=hp, dc=com
vlvGroupsScope SCOPE_SUB - The groups search for Virtual List View (VLV) API is a recursive search in the tree defined in vlvGroupsBase property.
SCOPE_ONE - The groups search for Virtual List View (VLV) API is performed across one level (direct children only) in the tree defined in vlvGroupsBase property.
SCOPE_BASE - The groups search for Virtual List View (VLV) API returns one entry maximum, as indicated in the vlvGroupsBase property.
Default:SCOPE_SUB
Example: vlvGroupsScope = SCOPE_SUB
vlvGroupsFilter Search filter, indicating what instances should be returned from the LDAP search for Virtual List View (VLV) API.
Default:(&(uid=*)(objectclass=inetOrgPerson))
Example:
vlvGroupsFilter = (|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\ (objectclass=accessGroup)(objectclass=accessRole))
vlvRolesBase Base dn (distinguished name) for users search.
Default:dc=example, dc=com
Example: vlvRolesBase = ou=People,dc=hp, dc=com
vlvRolesScope SCOPE_SUB - The roles search for Virtual List View (VLV) API is a recursive search in the tree defined in usersBase property.
SCOPE_ONE - The roles search for Virtual List View (VLV) API is performed across one level (direct children only) in the tree defined in usersBase property.
SCOPE_BASE - The roles search for Virtual List View (VLV) API returns one entry maximum, as indicated in the usersBase property.
Default: SCOPE_SUB
Example: vlvGroupsScope = SCOPE_SUB
vlvRolesFilter Search filter, indicating what instances should be returned from the LDAP search for Virtual List View (VLV) API.
Default: (&(uid=*)(objectclass=inetOrgPerson))
Example:
vlvRolesFilter = (|(objectclass=groupOfNames)(objectclass=groupOfUniqueNames)(objectclass=groupOfUrls)\(objectclass=accessGroup)(objectclass=accessRole))
usersCreationBase = ou=People,dc=hp, dc=com
groupsCreationBase = ou=Groups, dc=hp, dc=com
rolesCreationBase = ou=People,dc=hp, dc=comuumUserCreationAnd
DeletionAlloweduumUserEditingAllowed
uumGroupCreationAnd
DeletionAlloweduumGroupEditingAllowed
uumRoleCreationAnd
DeletionAlloweduumRoleEditingAllowed
UUM Metadata
Default:
uumUserCreationAndDeletionAllowed = trueuumUserEditingAllowed = true
uumGroupCreationAndDletionAllowed = true
uumGroupEditingAllowed = true
uumRoleCreationAndDeletionAllowed = true
uumRoleEditingAllowed = true
usersPasswordAttribute The user password attribute.
Example: usersPasswordAttribute = userPassword
ldapUseCache true - LDAP must use a cache.
false - LDAP should not use a cache.
Default: true
Example: ldapUseCache=true
ldapCacheSize The LDAP connection cache size in bytes. It represents an in-memory cache that can be used to reduce the number of search requests sent to the LDAP server.
Default: 1000000
Example: ldapCacheSize=1000000
ldapCacheTTL The LDAP connection cache life-time in seconds.
Default: 3600
Example: ldapCacheTTL=3600
-
bsf.properties.In the $HPBA_Home%glassfish/glassfish/domains/BTOA/config/conf/bsf.properties file, change:
From: To: personalization.provider=EXTERNAL personalization.provider=SHARED users.provider=EXTERNAL users.provider=SHARED groups.provider=EXTERNAL groups.provider=SHARED -
User synchronization. To improve the synchronization of users, perform the following:
- The synchronization of LDAP users, and Business Analytics and SAP BusinessObjects users is performed by default every 60 minutes (this is the recommended value).
To change the periodicity, click Admin > Scorecard > BA Settings, and enter a new value in the Users Info Reload Rate (minutes) in the Studio update area. Because each synchronization lasts a few minutes, it is recommended to set the default synchronization period so there is no overlap with the synchronization itself. For details, see Settings - BA Settings. - To make sure that the synchronization is only performed on the relevant users (for performance purposes). Make sure to add to the external-ldap.properties file located at
$HPBA_Home/glassfish/glassfish/domains/BTOA/config/conf, the (groupfilter=(&(objectClass=group)(cn=g-s-rbap-t-hpxs*)) so that only the users needed for Business Analytics are synchronized. -
Synchronize the LDAP users with SAP BusinessObjects, using one of the options below:
-
Option 1:
-
Log on to SAP ‘BusinessObjects BI platform Central Management Console’, and select Authentication> LDAP.
-
Check Update LDAP user groups and aliases now.
-
Click the Update button.
-
-
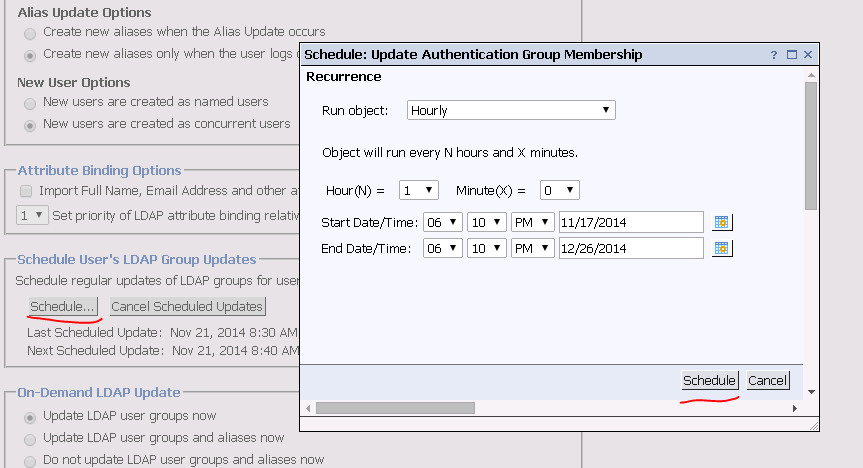
Option2: create a schedule to schedule regular updates of LDAP groups for users:
-
Log on to SAP ‘BusinessObjects BI platform Central Management Console’’, and select Authentication> LDAP.
-
Click the Schedule… button.
-
Input the schedule information.
-
Click the Schedule… button.
-
-
- The synchronization of LDAP users, and Business Analytics and SAP BusinessObjects users is performed by default every 60 minutes (this is the recommended value).
 LDAP Management Page
LDAP Management Page
Note You can combine using the LDAP Management user interface and the external-ldap.properties file to specify the parameters you need in order to work with LDAP.
Click  to refresh the page.
to refresh the page.
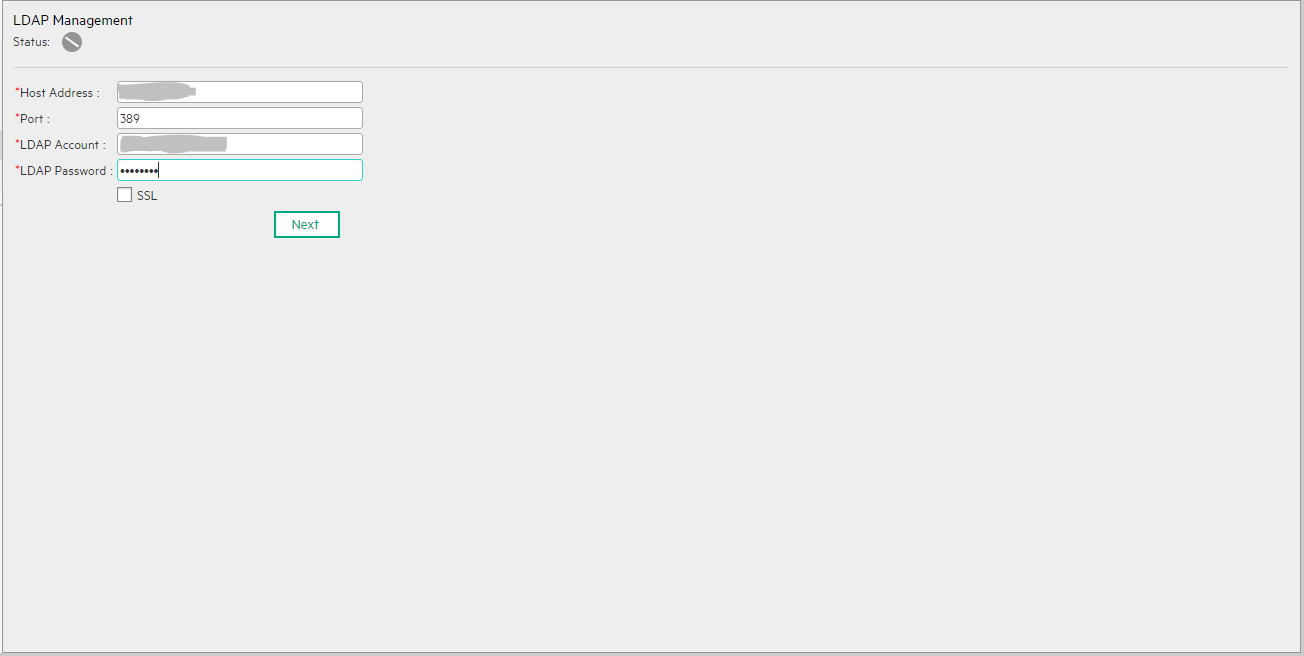
User interface elements are described below (when relevant, unlabeled elements are shown in angle brackets):
|
UI Element |
Description |
|---|---|
| Status |
|
| Host Address |
The name of the machine running the LDAP server. Default: localhost Example: ldap.hp.com |
| Port |
The port number of the machine running the LDAP server. Default: 389 Example: 636 |
| LDAP Account |
The Administrator logon name used for creating the initial LDAP connection. If the field is left empty, LDAP is access by anonymous user. There is no default Administrator user. Defaut: CN=Administrator Example: CN=Administrator |
| LDAP Password |
The Administrator logon password used for creating initial LDAPConnection. If the field is left empty, LDAP is access without a password. There is no default Administrator user password. Default: <empty_value> |
| SSL |
Select if the customer requires the SSL connection to LDAP. The SSL connection to the port defined in ldapPort property is attempted. If the server cannot perform the connection, the following error message is issued: The BA server cannot connect to the LDAP server.
In such a case, make sure that the relevant certificates are imported. After the import of the relevant certificates completes, restart the server. Defaut: unselected |
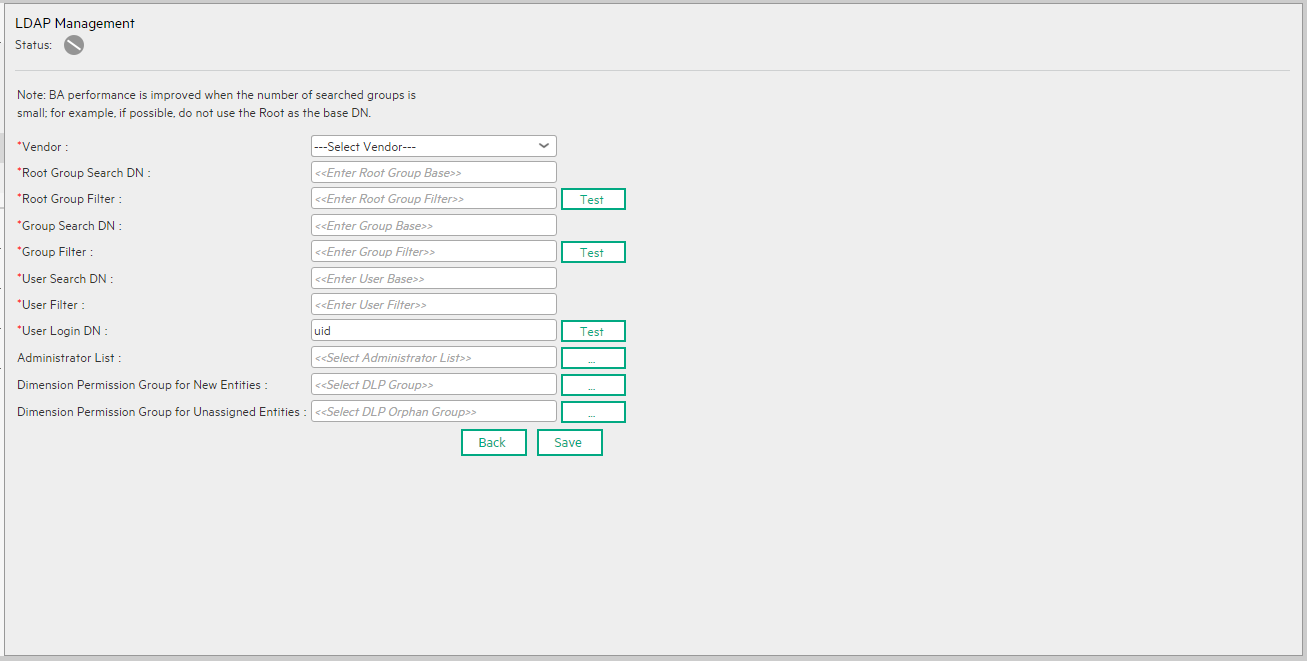
User interface elements are described below (when relevant, unlabeled elements are shown in angle brackets):
|
UI Element |
Description |
|---|---|
| Vendor |
Select the relevant vendor:
Only the above vendors are supported. |
| Root Group Search DN |
The base dn (distinguished name) for root groups search. For details on how to set this parameter, see Searches for LDAP user groups. Default: <usersBasevalue> Example: rootGroupsBase = ou=People,dc=hp, dc=com |
| Root Group Filter |
The search filter, indicating what instances should be returned from the LDAP search. For details on how to set this parameter, see Searches for LDAP user groups. Default: (|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole)) Example: rootGroupsFilter = Click Test to search for groups using the values you entered in the Root Group Filter and Root Group Search DN fields. After you click Test for theRoot Group Filter, the group filter is automatically filled. You can then modify it.
|
| Group Search DN |
The base dn (distinguished name) for groups search. For details on how to set this parameter, see Searches for LDAP user groups. Default: <userBase value> Example: groupsBase = ou=Groups,dc=hp, dc=com |
| Group Filter |
The search filter, indicating what instances should be returned from the LDAP search. For details on how to set this parameter, see Searches for LDAP user groups. Default: (|(objectclass=groupOfNames)(objecclass=groupOfUniqueNames)(objectclass=groupOfUrls)(objectclass=accessGroup)(objectclass=accessRole)) Example: groupsFilter = Click Test to search for groups using the values you entered in the Group Filter and Group Search DN fields.
|
| User Search DN |
The base DN (distinguished name) for users search. Default: dc=example, dc=com Example: usersBase = ou=People,dc=hp, dc=com |
| User Filter |
The search filter, indicating what instances should be returned from the LDAP search. Default: (&(uid=*)(objectclass=inetOrgPerson)) Example: usersFilter = (&(uid=*)(objectclass=inetOrgPerson)) Click Test to search for users using the values you entered in the User Filter and User Search DN fields.
|
| Administrator List |
After you transfer ITBA transfer to LDAP mode by clicking the Save button, ITBA fetches user information from the LDAP server. The first time, none of the LDAP users have ITBA Administrator permissions. So you must select at least one LDAP user to become the ITBA Administrator and to be able to manage users in ITBA. Click ... to select the users you want to be assigned ITBA Administrator permissions:
You can select more than one user. Their names are separated by semi-colons (;):
|
| Dimension Permission Group for New Entities |
Click ... and select the name of the default user group for new dimension entities. For details, see Users and Roles - Dimension Permissions. During the activation of LDAP, the default user group you selected is automatically entered in the corresponding Foundation settings. For details, see Settings - Foundation. |
| Dimension Permission Group for Unassigned Entities |
Click ... and select the name of the default user group for unassigned dimension entities after they have been unassigned. For details, see Users and Roles - Dimension Permissions. During the activation of LDAP, the default user group you selected is automatically entered in the corresponding Foundation settings. For details, see Settings - Foundation. |
| Save | Click Save to save your selection. The following warning is issued: Once the changes to the LDAP configuration are saved, restart the server. |
| Disable |
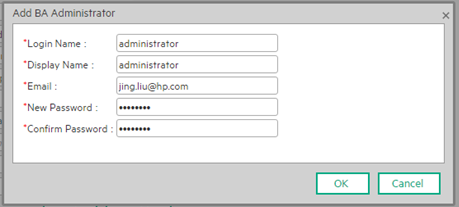
Click Disable to disable the LDAP configuration. Enter information about the ITBA Administrator in the dialog box that opens:
After the LDAP Admin disables the LDAP mode:
|
We welcome your comments!
To open the configured email client on this computer, open an email window.
Otherwise, copy the information below to a web mail client, and send this email to SW-Doc@hpe.com.
Help Topic ID:
Product:
Topic Title:
Feedback:









 The configuration is Disabled.
The configuration is Disabled.